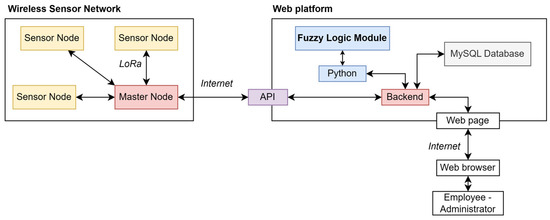
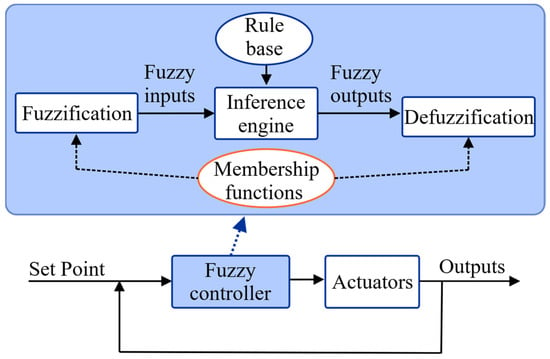
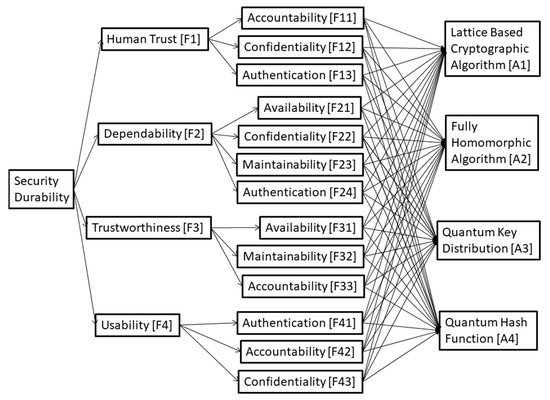
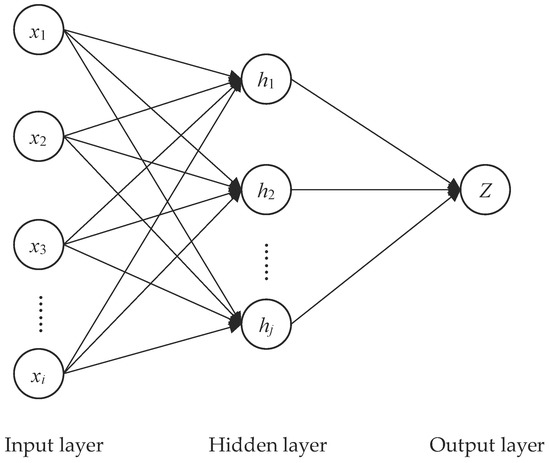
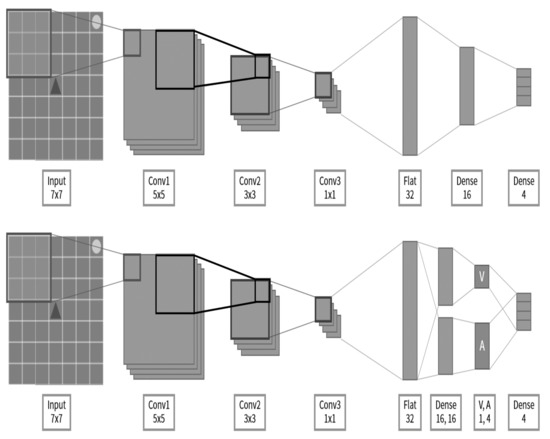
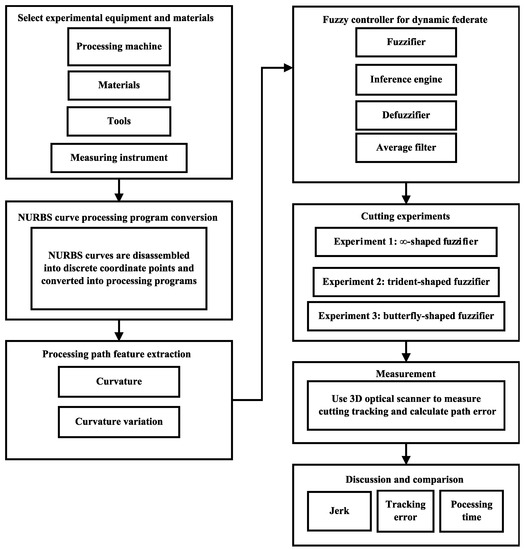
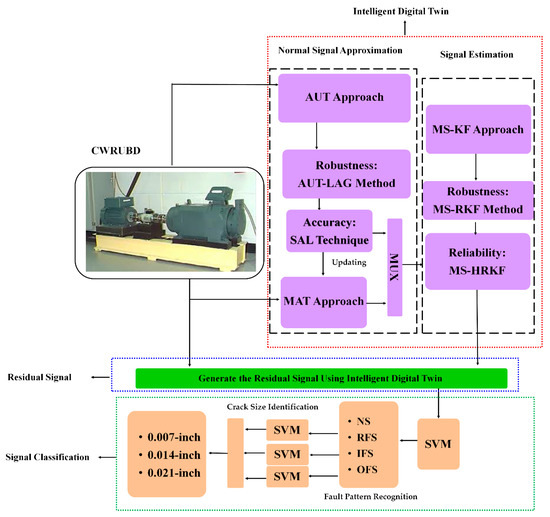
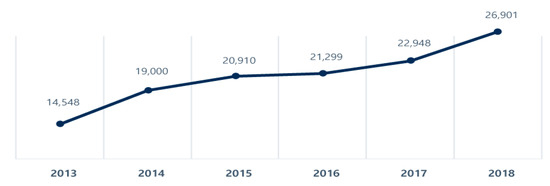
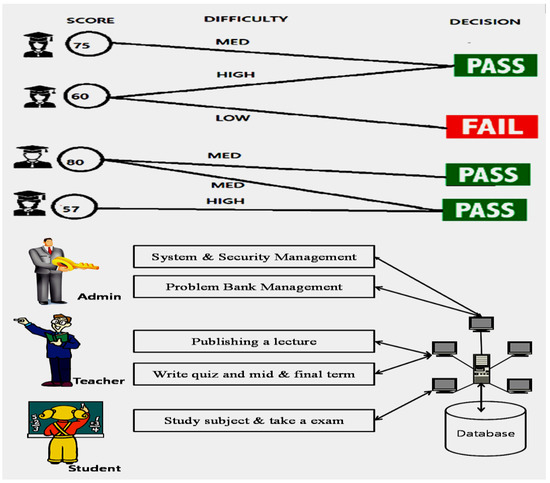
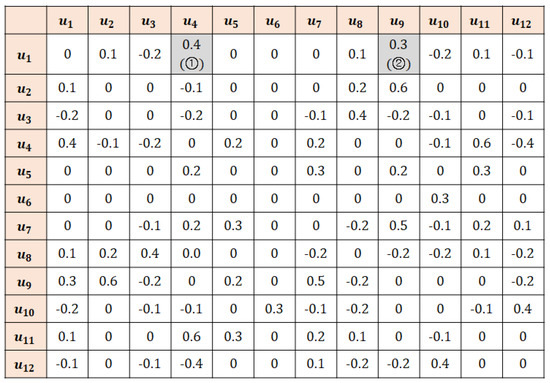
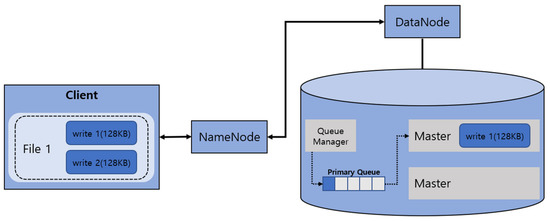
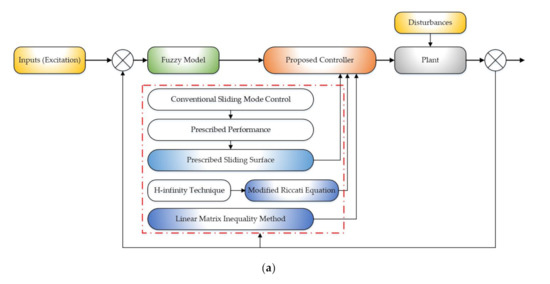
Dear Colleagues
Fuzzy systems are one of the most exciting fields of computing today. Over the past decades, fuzzy logic has become a solid part of everyday life and has been successfully used to solve real world problems.
The applications of fuzzy systems are very broad, including engineering, industrial, business, finance, medicine and many other areas.
Fuzzy systems cover a wide range of learning algorithms, including classical algorithms such as linear regression.
Development and application of fuzzy logic through support vector machines and neural networks or newly developed algorithms such as deep learning and boost tree models. Indeed, it is very difficult to properly determine the appropriate architecture and parameters of the fuzzy method so that the resulting learner model can achieve sound performance for both training and generalization.
The practical application of fuzzy systems poses additional challenges such as dealing with large, missing, distorted, and uncertain data. Also, interpretability is the most important characteristic that must be achieved if the fuzzy method is actually applied.
Interpretability allows you to understand fuzzy model behavior and increase confidence in the results.
This collection focuses on the application of fuzzy models in various fields and problems. Applied papers report practical results for various learning methods, discuss the conceptualization of problems, data representation, functional engineering, fuzzy models, critical comparisons with existing technologies, and interpretation of results.
Special attention will be paid to recently developed fuzzy methods such as deep learning and artificial intelligence.
This collection,”The Development and Application of Fuzzy Logic”, covers basic, applied, artificial intelligence, control, robotics, data analysis, data mining, decision making, finance and management, information systems, operational research, pattern recognition and image processing, In the field of soft computing and uncertainty modeling, we present a new development in the field of theory and application of fuzzy systems.
The anticipated submitted papers are expected to meet the theoretical release and increase in application and development using fuzzy system technology. New ideas that suggest a disruptive approach are also welcome.
Topics of interest include the following areas:
- Fuzzy genetic algorithm.
- Hybrid and fuzzy knowledge-based networks.
- Purge system and deep learning.
- Software engineering for fuzzy systems.
- Fuzzy systems in robotics and mechatronics.
- Fuzzy system application in signal processing.
- Patern Recognition's fuzzy system application.
- Fuzzy system application in communication.
- Artificial Intelligence.
Prof. Dr. Seongsoo Cho
Prof. Dr. Bhanu Shrestha
Guest Editors
Manuscript Submission Information
Manuscripts should be submitted online at www.mdpi.com by registering and logging in to this website. Once you are registered, click here to go to the submission form. Manuscripts can be submitted until the deadline. All submissions that pass pre-check are peer-reviewed. Accepted papers will be published continuously in the journal (as soon as accepted) and will be listed together on the collection website. Research articles, review articles as well as short communications are invited. For planned papers, a title and short abstract (about 100 words) can be sent to the Editorial Office for announcement on this website.
Submitted manuscripts should not have been published previously, nor be under consideration for publication elsewhere (except conference proceedings papers). All manuscripts are thoroughly refereed through a single-blind peer-review process. A guide for authors and other relevant information for submission of manuscripts is available on the Instructions for Authors page. Applied Sciences is an international peer-reviewed open access semimonthly journal published by MDPI.
Please visit the Instructions for Authors page before submitting a manuscript.
The Article Processing Charge (APC) for publication in this open access journal is 2400 CHF (Swiss Francs).
Submitted papers should be well formatted and use good English. Authors may use MDPI's
English editing service prior to publication or during author revisions.