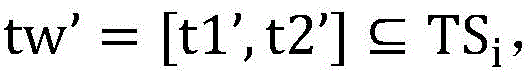CN114741711A - Multi-keyword searchable encryption method based on block chain - Google Patents
Multi-keyword searchable encryption method based on block chain Download PDFInfo
- Publication number
- CN114741711A CN114741711A CN202210355792.9A CN202210355792A CN114741711A CN 114741711 A CN114741711 A CN 114741711A CN 202210355792 A CN202210355792 A CN 202210355792A CN 114741711 A CN114741711 A CN 114741711A
- Authority
- CN
- China
- Prior art keywords
- retrieval
- keyword
- user
- trapdoor
- data owner
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Granted
Links
- 238000000034 method Methods 0.000 title claims abstract description 52
- 238000012795 verification Methods 0.000 claims abstract description 24
- 238000004364 calculation method Methods 0.000 claims description 20
- 230000008569 process Effects 0.000 claims description 20
- 230000006870 function Effects 0.000 claims description 10
- 238000010276 construction Methods 0.000 claims description 9
- 125000004122 cyclic group Chemical group 0.000 claims description 2
- 230000000717 retained effect Effects 0.000 claims 1
- 230000007246 mechanism Effects 0.000 abstract description 8
- 230000006399 behavior Effects 0.000 abstract description 6
- 238000004458 analytical method Methods 0.000 abstract description 4
- 238000002474 experimental method Methods 0.000 description 6
- 238000011160 research Methods 0.000 description 5
- 238000010586 diagram Methods 0.000 description 4
- 238000005516 engineering process Methods 0.000 description 3
- 230000009286 beneficial effect Effects 0.000 description 1
- 230000000052 comparative effect Effects 0.000 description 1
- 238000013500 data storage Methods 0.000 description 1
- 230000006872 improvement Effects 0.000 description 1
- 230000003993 interaction Effects 0.000 description 1
- 238000007726 management method Methods 0.000 description 1
- 238000010845 search algorithm Methods 0.000 description 1
Images
Classifications
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/60—Protecting data
- G06F21/602—Providing cryptographic facilities or services
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F16/00—Information retrieval; Database structures therefor; File system structures therefor
- G06F16/10—File systems; File servers
- G06F16/13—File access structures, e.g. distributed indices
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F16/00—Information retrieval; Database structures therefor; File system structures therefor
- G06F16/10—File systems; File servers
- G06F16/14—Details of searching files based on file metadata
- G06F16/148—File search processing
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L9/00—Cryptographic mechanisms or cryptographic arrangements for secret or secure communications; Network security protocols
- H04L9/08—Key distribution or management, e.g. generation, sharing or updating, of cryptographic keys or passwords
- H04L9/0816—Key establishment, i.e. cryptographic processes or cryptographic protocols whereby a shared secret becomes available to two or more parties, for subsequent use
- H04L9/085—Secret sharing or secret splitting, e.g. threshold schemes
Landscapes
- Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- General Engineering & Computer Science (AREA)
- General Physics & Mathematics (AREA)
- Physics & Mathematics (AREA)
- Computer Security & Cryptography (AREA)
- Databases & Information Systems (AREA)
- Data Mining & Analysis (AREA)
- Library & Information Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Health & Medical Sciences (AREA)
- Bioethics (AREA)
- General Health & Medical Sciences (AREA)
- Computer Hardware Design (AREA)
- Software Systems (AREA)
- Information Retrieval, Db Structures And Fs Structures Therefor (AREA)
Abstract
Description
技术领域technical field
本发明涉及区块链技术领域,尤其涉及一种基于区块链的多关键字可搜索加密方法。The invention relates to the technical field of blockchain, in particular to a multi-keyword searchable encryption method based on blockchain.
背景技术Background technique
云计算近年来得到了蓬勃发展,大量公司开始向社会提供云服务。云服务种类包括平台即服务、基础设施即服务和软件即服务。用户可以根据自身需要选择购买或租用不同的云服务。越来越多的机构也开始将数据和应用转移到云服务器中。Cloud computing has been booming in recent years, and a large number of companies have begun to provide cloud services to the society. Cloud service categories include platform-as-a-service, infrastructure-as-a-service, and software-as-a-service. Users can choose to buy or rent different cloud services according to their own needs. More and more organizations are also moving data and applications to cloud servers.
云服务带来更多便利的同时,其存在的安全和隐私泄露风险也不容忽视。个人用户最常用的就是租用云存储服务器存储个人数据。例如苹果公司的iCloud。用户可以将手机中的照片、视频和其他类型的文件存储在iCloud云服务器中。这在节约本地存储空间的同时,用户可以不限设备随时随地查看iCloud中的文件。While cloud services bring more convenience, the risks of security and privacy leakage cannot be ignored. The most commonly used by individual users is to rent cloud storage servers to store personal data. For example, Apple's iCloud. Users can store photos, videos and other types of files on their phones in the iCloud cloud server. This saves local storage space, and users can view files in iCloud anytime, anywhere without restrictions on devices.
但由于这些信息都是明文存储在云服务器中的,数据一旦泄露,将对用户的隐私造成严重侵害。通过将数据加密后上传至云服务器能够保护数据安全,但对数据的管理和使用带来了不便,特别是用户使用较频繁的检索操作。However, since these information are stored in the cloud server in clear text, once the data is leaked, it will cause serious damage to the privacy of users. The data security can be protected by encrypting the data and uploading it to the cloud server, but it brings inconvenience to the management and use of the data, especially the retrieval operations that users use more frequently.
为了实现在密文上的关键字搜索,学者们提出了可搜索加密。现有可搜索加密方案的研究中,对算法的表达能力的提升是重要的研究方向。其中多关键字检索是研究的热点,学者探索了支持逻辑连接的关键字检索方案,或者利用kNN(K-NearestNeighbor)、Word2vec等技术来计算和评估关键字与密文文档的相似程度,实现多关键字检索。学者们还提出了更方便的模糊检索方案。In order to realize keyword search on ciphertext, scholars have proposed searchable encryption. In the existing research on searchable encryption schemes, the improvement of the expressive ability of the algorithm is an important research direction. Among them, multi-keyword retrieval is a research hotspot. Scholars have explored keyword retrieval schemes that support logical connections, or use technologies such as kNN (K-Nearest Neighbor) and Word2vec to calculate and evaluate the similarity between keywords and ciphertext documents. Keyword search. Scholars have also proposed more convenient fuzzy retrieval schemes.
然而除模糊检索外,现有的多关键字可搜索加密方案只能提供精确结果并在此基础上实现对检索结果的排序。当用户检索的多个关键字没有对应的文档时检索结果为空,用户体验较差。However, except for fuzzy retrieval, the existing multi-keyword searchable encryption schemes can only provide accurate results and can sort retrieval results on this basis. When multiple keywords retrieved by the user do not have corresponding documents, the retrieval result is empty, and the user experience is poor.
大量可搜索加密方案中假设云服务器是诚实的,在实际应用中云服务可能是不诚实的或恶意的,其提供的检索结果不可靠。因此引入对检索结果的验证机制,从而防范云服务器恶意行为也是可搜索加密方案的重要研究方向,其中基于区块链的可搜索加密方案是研究的热点。但这些可搜索加密方案中云服务器为逻辑上的单一节点,中心化程度较高,而且不能杜绝云服务器的恶意行为。例如,当云服务器恶意返回空结果时,可能会使最终的检索结果为空。A large number of searchable encryption schemes assume that cloud servers are honest. In practical applications, cloud services may be dishonest or malicious, and the retrieval results provided by them are unreliable. Therefore, the introduction of a verification mechanism for retrieval results to prevent malicious behavior of cloud servers is also an important research direction of searchable encryption schemes, among which the searchable encryption scheme based on blockchain is a research hotspot. However, in these searchable encryption schemes, the cloud server is a logically single node, with a high degree of centralization, and cannot prevent malicious behavior of the cloud server. For example, when the cloud server maliciously returns empty results, the final retrieval result may be empty.
目前大量可搜索加密方案中均假设服务器是诚实的,但在实际应用中,云服务器可能会由出于成本考虑,在方案运行过程中出现不诚实的行为。例如返回不完整的检索结果以减少流量消耗,也可能返回随机结果或空结果以节约计算资源。这对用户与云服务器之间的交易公平存在很大损害,需要引入对检索结果的验证机制。At present, a large number of searchable encryption schemes assume that the server is honest, but in practical applications, the cloud server may behave dishonestly during the operation of the scheme due to cost considerations. For example, incomplete search results are returned to reduce traffic consumption, and random results or empty results may be returned to save computing resources. This greatly damages the fairness of transactions between users and cloud servers, and a verification mechanism for retrieval results needs to be introduced.
区块链技术的应用能够有效解决这一问题。区块链中的数据不可篡改,且可验证可追溯。区块链能够作为可信方对检索结果进行验证,从而保证交易公平。The application of blockchain technology can effectively solve this problem. The data in the blockchain cannot be tampered with and can be verified and traced. The blockchain can act as a trusted party to verify the retrieval results, thus ensuring fair transactions.
现有方案中通过区块链建立的验证机制在一定程度上保证了交易公平,但这些方案中云服务器依然是逻辑上的单一节点,去中心化程度不够高。当云服务器出现恶意行为,只能通过扣除押金的方式进行惩罚,在方案的运行中依然需要依赖有过恶意行为的云服务器。The verification mechanism established by the blockchain in the existing schemes ensures the fairness of the transaction to a certain extent, but the cloud server in these schemes is still a single logical node, and the degree of decentralization is not high enough. When a cloud server behaves maliciously, it can only be punished by deducting the deposit. In the operation of the scheme, it is still necessary to rely on the cloud server with malicious behavior.
发明内容SUMMARY OF THE INVENTION
本发明所要解决的技术问题是如何提供一种能够提高检索效率、保证交易公平以及具有较高灵活性的基于区块链的多关键字可搜索加密方法。The technical problem to be solved by the present invention is how to provide a blockchain-based multi-keyword searchable encryption method that can improve retrieval efficiency, ensure transaction fairness and have higher flexibility.
为解决上述技术问题,本发明所采取的技术方案是:一种基于区块链的多关键字可搜索加密方法,其特征在于:In order to solve the above-mentioned technical problems, the technical scheme adopted by the present invention is: a multi-keyword searchable encryption method based on blockchain, which is characterized in that:
初始化:数据所有者生成公共参数和密钥,并创建智能合约,将公共参数和公钥公开,将私钥保密;Initialization: The data owner generates public parameters and keys, and creates a smart contract, making public parameters and public keys public, and keeping private keys secret;
索引构建:数据所有者生成密文文件、索引、共享密钥和其他参数,将生成的密文文件发送至存储服务器,将索引发送至搜索服务器,将共享密钥发送给其他用户,将生成的其他参数保密;Index construction: The data owner generates the ciphertext file, index, shared key and other parameters, sends the generated ciphertext file to the storage server, sends the index to the search server, sends the shared key to other users, and sends the generated ciphertext file to the storage server. Other parameters are kept secret;
陷门生成:用户将需要检索的多个关键字生成检索陷门,并发起检索请求;Trapdoor generation: The user generates retrieval trapdoors from multiple keywords that need to be retrieved, and initiates retrieval requests;
分发:智能合约将用户的检索请求分解后发送给各个搜索服务器;Distribution: The smart contract decomposes the user's retrieval request and sends it to each search server;
检索:搜索服务器处理检索请求,将得到的检索结果发送给用户和智能合约;Retrieval: The search server processes the retrieval request and sends the retrieved results to the user and the smart contract;
验证:智能合约对检索结果进行验证,对验证失败的结果发起仲裁请求;Verification: The smart contract verifies the retrieval results, and initiates an arbitration request for the results that fail to verify;
解密:用户根据检索结果进行计算,根据计算结果向存储服务器请求对应的密文文件,将密文文件解密后得到对应的明文文件,如果计算或解密失败则发起仲裁请求;Decryption: The user calculates according to the retrieval result, requests the corresponding ciphertext file from the storage server according to the calculation result, decrypts the ciphertext file to obtain the corresponding plaintext file, and initiates an arbitration request if the calculation or decryption fails;
仲裁:数据所有者处理仲裁请求,校验检索结果。Arbitration: The data owner processes the arbitration request and verifies the retrieval results.
采用上述技术方案所产生的有益效果在于:1)本申请所述方法使用去中心化的多服务器架构,将数据存储和数据检索分别交由多个云服务器。在此基础上设计了分发算法,能够将包含多关键字的检索任务分解后分发给多个搜索服务器执行,提高了检索效率,同时实现了负载均衡。The beneficial effects of adopting the above technical solutions are: 1) The method described in this application uses a decentralized multi-server architecture, and transfers data storage and data retrieval to multiple cloud servers respectively. On this basis, a distribution algorithm is designed, which can decompose the retrieval tasks containing multiple keywords and distribute them to multiple search servers for execution, which improves the retrieval efficiency and achieves load balancing.
2)本申请所述方法中设计了验证算法和仲裁算法,能够验证检索结果,防范云服务器的恶意行为,保证交易公平。在检索算法中引入关键字权重机制,能够在检索结果为空时将权重最高的模糊结果返回给用户,灵活性更强。2) A verification algorithm and an arbitration algorithm are designed in the method described in this application, which can verify the retrieval result, prevent malicious behavior of the cloud server, and ensure fair transaction. The keyword weight mechanism is introduced into the retrieval algorithm, which can return the fuzzy result with the highest weight to the user when the retrieval result is empty, which is more flexible.
3)在真实数据集上对本申请进行了对比实验,证明了本申请具有较高的效率。3) Comparative experiments are carried out on the application on the real data set, which proves that the application has high efficiency.
附图说明Description of drawings
下面结合附图和具体实施方式对本发明作进一步详细的说明。The present invention will be described in further detail below with reference to the accompanying drawings and specific embodiments.
图1是本发明实施例所述方法的模型图;1 is a model diagram of the method according to an embodiment of the present invention;
图2是本发明实施例所述方法的流程图;Fig. 2 is the flow chart of the method described in the embodiment of the present invention;
图3是本发明实施例中索引构建阶段耗时对比图;3 is a time-consuming comparison diagram of an index construction stage in an embodiment of the present invention;
图4是本发明实施例中陷门生成阶段耗时对比图;4 is a time-consuming comparison diagram of a trapdoor generation stage in an embodiment of the present invention;
图5是本发明实施例中关键字检索阶段耗时对比图;5 is a time-consuming comparison diagram of a keyword retrieval stage in an embodiment of the present invention;
图6是本发明实施例中搜索服务器数量对所述方法总耗时的影响图。FIG. 6 is a graph showing the influence of the number of search servers on the total time consumption of the method in an embodiment of the present invention.
具体实施方式Detailed ways
下面结合本发明实施例中的附图,对本发明实施例中的技术方案进行清楚、完整地描述,显然,所描述的实施例仅仅是本发明的一部分实施例,而不是全部的实施例。基于本发明中的实施例,本领域普通技术人员在没有做出创造性劳动前提下所获得的所有其他实施例,都属于本发明保护的范围。The technical solutions in the embodiments of the present invention will be clearly and completely described below with reference to the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only a part of the embodiments of the present invention, rather than all the embodiments. Based on the embodiments of the present invention, all other embodiments obtained by those of ordinary skill in the art without creative efforts shall fall within the protection scope of the present invention.
在下面的描述中阐述了很多具体细节以便于充分理解本发明,但是本发明还可以采用其他不同于在此描述的其它方式来实施,本领域技术人员可以在不违背本发明内涵的情况下做类似推广,因此本发明不受下面公开的具体实施例的限制。Many specific details are set forth in the following description to facilitate a full understanding of the present invention, but the present invention can also be implemented in other ways different from those described herein, and those skilled in the art can do so without departing from the connotation of the present invention. Similar promotion, therefore, the present invention is not limited by the specific embodiments disclosed below.
本申请实施例中公开了一个基于区块链的多关键字可搜索加密方法,如图1所示:The embodiment of this application discloses a blockchain-based multi-keyword searchable encryption method, as shown in Figure 1:
本申请实施例的参与方包括数据所有者(DO)、存储服务器(S_Store)、搜索服务器(S_Search)、用户(DU),均作为区块链节点。数据所有者负责对文档进行加密生成密文数据并建立索引。存储服务器负责存储数据所有者生成的密文数据。搜索服务器负责存储索引数据,并根据用户上传的检索陷门计算和检索对应的索引数据。用户根据自身检索需要计算生成检索陷门,并通过区块链将其发送给搜索服务器,获取对应的索引数据。用户根据索引数据向存储服务器请求对应的密文数据。The participants in the embodiments of the present application include a data owner (DO), a storage server (S_Store), a search server (S_Search), and a user (DU), all of which serve as blockchain nodes. The data owner is responsible for encrypting documents to generate ciphertext data and indexing. The storage server is responsible for storing ciphertext data generated by the data owner. The search server is responsible for storing the index data, and calculating and retrieving the corresponding index data according to the retrieval trapdoor uploaded by the user. Users calculate and generate retrieval trapdoors according to their own retrieval needs, and send them to the search server through the blockchain to obtain the corresponding index data. The user requests the corresponding ciphertext data from the storage server according to the index data.
本申请包括以下8个多项式时间算法:This application includes the following 8 polynomial time algorithms:
1)初始化算法Setup(λ)→(pub,PDO,SDO,Pu,Su)。算法以安全参数λ为输入,数据所有者生成公共参数pub,并将智能合约部署在区块链上。数据所有者和其他用户生成公私钥对,将私钥SDO和Su保密,将公钥PDO和Pu公开;1) Initialization algorithm Setup(λ)→(pub, P DO , S DO , P u , S u ). The algorithm takes the security parameter λ as input, the data owner generates the public parameter pub, and deploys the smart contract on the blockchain. The data owner and other users generate a public-private key pair, keep the private keys S DO and S u secret, and make public the public keys P DO and P u ;
2)索引构建算法Buildindex(pub,W,M,SDO)→(C,I,Key,VC,VRs,VRu)。算法以公开参数pub,明文关键字集合W,明文文件集合M和数据所有者私钥SDO为输入,输出密文文件集合C,密文索引I,共享密钥Key以及用于结果校验的集合VC,VRs,VRu。算法由数据所有者执行,对于集合C与索引I分别发送至存储服务器和搜索服务器,将搜索密钥Key发送至其他用户,将生成的集合VC公开在区块链上,集合VRs和VRu保密。2) Index building algorithm Buildindex(pub, W, M, S DO )→(C, I, Key, VC, VRs, VRu). The algorithm takes the public parameter pub, the set of plaintext keywords W, the set of plaintext files M and the private key SDO of the data owner as input, and outputs the set of ciphertext files C, the ciphertext index I, the shared key Key, and the key used for result verification. Collection VC, VRs, VRu. The algorithm is executed by the data owner. The set C and index I are sent to the storage server and the search server respectively, the search key Key is sent to other users, the generated set VC is published on the blockchain, and the sets VRs and VRu are kept secret.
3)陷门生成算法GenTrapdoor(Key,W’,Su,PDO)→Tw。算法以搜索密钥Key,待检索关键字集合W’,用户私钥Su和数据所有者公钥PDO为输入,生成陷门集合Tw后将其发送至智能合约。算法由用户执行,在执行时可为每个关键字指定权重。3) Trapdoor generation algorithm GenTrapdoor(Key,W',S u ,P DO )→Tw. The algorithm takes the search key Key, the set of keywords to be retrieved W', the user's private key S u and the data owner's public key P DO as input, generates the trapdoor set Tw and sends it to the smart contract. The algorithm is executed by the user, where each keyword can be assigned a weight.
4)分发算法Distribute(Tw)→({TS1,TS2,TS3,…})。算法以用户发送的陷门集合Tw为输入,智能合约执行该算法输出分解后的陷门集合{TS1,TS2,TS3,…},其中 4) Distribution algorithm Distribute(Tw)→({TS 1 , TS 2 , TS 3 ,...}). The algorithm takes the trapdoor set Tw sent by the user as input, and the smart contract executes the algorithm to output the decomposed trapdoor set {TS 1 , TS 2 , TS 3 ,…}, where
5)检索算法Search(TSi,I,Pu)→(RSi,R_TSi)。算法以陷门集合TSi,密文索引I,用户公钥Pu为输入,各个搜索服务器执行该算法输出检索结果RSi和R_TSi。5) Search algorithm Search(TS i ,I,P u )→(RS i ,R_TS i ). The algorithm takes trapdoor set TS i , ciphertext index I, and user public key Pu as input, and each search server executes the algorithm to output retrieval results RS i and R_TS i .
6)验证算法Verify(RSi)→{0,1}。算法由智能合约执行,算法以各个搜索服务器发送的检索结果RSi为输入,输出验证结果,并根据验证结果发送押金和服务费。6) Verify algorithm Verify(RS i )→{0,1}. The algorithm is executed by the smart contract. The algorithm takes the retrieval result RS i sent by each search server as input, outputs the verification result, and sends the deposit and service fee according to the verification result.
7)解密算法Dec(R_TSi,PDO,Key)→M。算法由用户执行,以检索结果R_TSi,数据所有者公钥PDO,搜索密钥Key为输入,得到检索结果对应的明文文件M。7) Decryption algorithm Dec(R_TS i , P DO , Key)→M. The algorithm is executed by the user to obtain the plaintext file M corresponding to the retrieval result by taking the retrieval result R_TS i , the data owner public key P DO , and the search key Key as input.
8)仲裁算法Arbitrate(w”,Nw”,x)→{0,1}。算法由数据所有者执行,以待仲裁的检索结果Nw”,待仲裁的关键字w”(可选),秘密信息x为输入,输出验证结果。8) Arbitration algorithm Arbitrate(w",Nw",x)→{0,1}. The algorithm is executed by the data owner, and takes the retrieval result Nw" to be arbitrated, the keyword w" to be arbitrated (optional), the secret information x as input, and outputs the verification result.
如图2所示,本发明实施例公开了一种基于区块链的多关键字可搜索加密方法,所述方法中包括的8个多项式时间算法的具体内容及执行流程如下所述:As shown in FIG. 2 , an embodiment of the present invention discloses a blockchain-based multi-keyword searchable encryption method. The specific content and execution flow of the eight polynomial time algorithms included in the method are as follows:
初始化算法:Setup(λ)→(pub,PDO,SDo,Pu,Su)。Initialization algorithm: Setup(λ)→(pub,P DO ,S Do ,P u ,S u ).
本申请首先需要执行初始化算法Setup(),对应于图2中步骤①。该算法的执行过程如下:This application first needs to execute the initialization algorithm Setup( ), which corresponds to step ① in FIG. 2 . The execution of the algorithm is as follows:
1)数据所有者生成两个阶为素数p的乘法循环群G1和G2,g为G1的生成元。生成一个双线性映射e:G1×G1→G2。选择伪随机函数F∶{0,1}*→{0,1}k。选择两个密码哈希函数H1:{0,1}*→G1与H2:G2→{0,1}k,k为整数。选择抗碰撞哈希函数H3:{0,1}*→{0,1}k,H4:{0,1}*→{0,1}k。选择对称加密算法(Enc,Dec)。数据所有者公布系统公共参数pub={p,G1,G2,e,F,H1,H2,H3,H4,(Enc,Dec)},并将其发布至区块链。1) The data owner generates two multiplicative cyclic groups G 1 and G 2 whose order is prime p, and g is the generator of G 1 . Generate a bilinear map e: G 1 ×G 1 →G 2 . Choose a pseudorandom function F: {0,1} * →{0,1} k . Choose two cryptographic hash functions H 1 :{0,1} * →G 1 and H 2 :G 2 →{0,1} k , where k is an integer. The collision-resistant hash functions H 3 :{0,1} * →{0,1} k , H 4 :{0,1} * →{0,1} k are chosen. Select a symmetric encryption algorithm (Enc, Dec). The data owner publishes the system public parameters pub={p, G 1 , G 2 , e, F, H 1 , H 2 , H 3 , H 4 , (Enc, Dec)}, and publishes them to the blockchain.
数据所有者随机选取s∈Zp计算SDO=gs作为私钥,并计算公钥用户随机选取u∈Zp,计算作为私钥,计算用户公钥Pu=gu。数据所有者和用户将私钥保存,将公钥作为公开信息发布至区块链。The data owner randomly selects s ∈ Z p to calculate S DO = g s as the private key, and calculates the public key The user randomly selects u∈Zp and calculates As the private key, the user public key P u = gu is calculated. Data owners and users save the private key and publish the public key to the blockchain as public information.
2)数据所有者创建智能合约并将其发布至区块链。用户及搜索服务器在方案执行过程中需要调用智能合约以完成整个检索过程。智能合约的功能包括:暂存用户服务费和搜索服务器的押金;分解和发送检索任务;验证检索结果。在每次检索完成后,用户可提取智能合约中扣留的押金。2) The data owner creates a smart contract and publishes it to the blockchain. The user and the search server need to call the smart contract during the execution of the solution to complete the entire retrieval process. The functions of the smart contract include: temporarily storing the user service fee and the deposit of the search server; decomposing and sending retrieval tasks; and verifying the retrieval results. After each retrieval is completed, the user can withdraw the deposit held in the smart contract.
索引构建算法:Buildindex(pub,W,M,SDO)→(C,I,Key,VC,VRs,VRu)。Index building algorithm: Buildindex(pub,W,M,S DO )→(C,I,Key,VC,VRs,VRu).
初始化完成后,数据所有者需要执行Buildindex()算法,对应于图2中步骤②。该算法执行过程如下:After the initialization is completed, the data owner needs to execute the Buildindex() algorithm, which corresponds to step ② in Figure 2. The algorithm execution process is as follows:
1)数据所有者将明文文件进行关键字拆分,得到关键字集合W={w1,w2,w3,…}。数据所有者使用对称算法加密明文文件得到密文文件。随机选取x∈Zp,对于明文文件Mi,其密文文件Ci=Enc(Mi,k),k为对称密钥,k=H2(e(g,gx))。密文文件集合为C={C1,C2,C3,…},对于文件Ci,将密文文件排序后按照序号i分配文件编号FNi=2i-1,并计算H4(Ci),得到集合VC={[FN1,H4(C1)],[FN2,H4(C2)],…,[FNi,H4(Ci)]}。数据所有者将所有密文文件C及其编号发送至存储服务器,将VC发布至区块链。此时密文文件的哈希值均锚定在区块链上,可以用于校验检索结果。1) The data owner splits the plaintext file by keywords to obtain a keyword set W={w 1 , w 2 , w 3 ,...}. The data owner uses a symmetric algorithm to encrypt the plaintext file to obtain the ciphertext file. Randomly select x∈Z p , for the plaintext file M i , the ciphertext file C i =Enc(M i ,k), k is the symmetric key, k=H 2 (e(g,g x )). The set of cipher text files is C={C 1 , C 2 , C 3 ,...}, for the files C i , after sorting the cipher text files, assign the file number FN i =2 i-1 according to the sequence number i, and calculate H 4 ( C i ), the set VC={[FN 1 , H 4 (C 1 )], [FN 2 , H 4 (C 2 )], . . . , [FN i , H 4 (C i )]} is obtained. The data owner sends all ciphertext files C and their numbers to the storage server, and publishes VC to the blockchain. At this time, the hash value of the ciphertext file is anchored on the blockchain and can be used to verify the retrieval result.
2)数据所有者利用密文文件编号及其对应的关键字,构建关键字-文档编号文件索引I,计算过程如下:2) The data owner utilizes the ciphertext file number and its corresponding keyword to construct the keyword-document number file index I, and the calculation process is as follows:
设包含关键字w的密文文件编号集合为{FN1,FN2,FN3,…}。Let the set of ciphertext file numbers containing the keyword w be {FN 1 , FN 2 , FN 3 ,…}.
2-1)利用关键字w,计算y=H3(w)。2-1) Using the keyword w, calculate y=H 3 (w).
2-2)计算Cw=e(gx,gy)=e(g,g)xy。2-2) Calculate C w =e(g x , gy )=e(g,g) xy .
2-3)令Key=gsx,计算b=F(Key)。2-3) Let Key=g sx and calculate b=F(Key).
2-4)计算verify_bit=e(H1(w),Key)mod 2。2-4) Calculate verify_bit=e(H 1 (w), Key)
2-5)计算聚合后的文件编号Nw=FN1&FN2&FN3&…,并将verify_bit插入到Nw的第b个比特位中,&表示与运算。2-5) Calculate the aggregated file number Nw=FN 1 &FN 2 &FN 3 &..., and insert the verify_bit into the b-th bit of Nw, and & represents an AND operation.
关键字w对应的索引为Iw=[Cw,Nw]。数据所有者对关键字集合W中的每个关键字均执行以上操作,生成索引I={Iw1,Iw2,…},之后将索引上传至各个搜索服务器。同时,数据所有者计算VN=H4(Nw||x),Vw=H4(w||Nw||x)生成集合VRs={VN1,VN2,VN3,…}和VRu={Vw1,Vw2,Vw3,…},用于对有争议的检索结果进行仲裁。The index corresponding to the keyword w is Iw=[Cw, Nw]. The data owner performs the above operations on each keyword in the keyword set W, generates an index I={Iw 1 , Iw 2 , ...}, and then uploads the index to each search server. At the same time, the data owner calculates VN=H 4 (Nw||x), Vw=H 4 (w||Nw||x) to generate the set VRs={VN 1 , VN 2 , VN 3 ,…} and VRu={ Vw 1 , Vw 2 , Vw 3 ,…} for arbitration of disputed search results.
3)数据所有者将共享密钥Key=gsx发至各个用户,用户必须利用此密钥才能构造合法的检索陷门。数据所有者将x,VRs,VRu,SDO作为秘密信息保存。3) The data owner sends the shared key Key=g sx to each user, and the user must use this key to construct a legal retrieval trapdoor. Data owners keep x, VRs, VRu, S DO as secret information.
陷门生成算法:GenTrapdoor(Key,W’,Su,PDO)→Tw。Trapdoor generation algorithm: GenTrapdoor(Key,W',S u ,P DO )→Tw.
用户需要执行GenTrapdoor()算法将需要检索的关键字生成检索陷门,对应于图2中步骤③。该算法的执行过程如下:The user needs to execute the GenTrapdoor() algorithm to generate a search trapdoor for the keywords to be searched, which corresponds to step ③ in Figure 2. The execution of the algorithm is as follows:
1)设待检索关键字集合为W′={w1,w2,w3,…},用户需要同时为每个关键字指定权重p,得到集合Wp={[w1,p1],[w2,p2],[w3,p3],…}。权重代表各个关键字的检索优先级,主要用于在检索结果为空时计算模糊结果,权重越高的关键字包含在检索结果中的可能性越大。如用户不指定权重,则默认按照顺序分配,pi=2i,i为关键字序号。1) Set the set of keywords to be retrieved as W′={w 1 ,w 2 ,w 3 ,…}, the user needs to specify the weight p for each keyword at the same time, and obtain the set W p ={[w 1 ,p 1 ] ,[w 2 ,p 2 ],[w 3 ,p 3 ],…}. The weight represents the retrieval priority of each keyword, and is mainly used to calculate fuzzy results when the retrieval result is empty. Keywords with higher weights are more likely to be included in the retrieval results. If the user does not specify the weight, it will be assigned in order by default, p i =2 i , and i is the keyword sequence number.
对于关键字w∈W′,其陷门的计算过程如下:For the keyword w∈W′, the calculation process of the trapdoor is as follows:
1-1)计算y=H3(w)。1-1) Calculate y=H 3 (w).
1-2)随机选取r∈Zp,计算t2=e(Key·gy·gr,PDO)=e(grsxy,PDO)=e(g,g)rxy。1-2) Randomly select r∈Z p , calculate t2=e(Key· gy ·g r , P DO )=e(g rsxy , P DO )=e(g,g) rxy .
1-3)关键字w的检索陷门 1-3) Search trapdoor for keyword w
2)对每个待检索关键字执行以上操作后得到陷门集合Tw={[tw1,p1],[tw2,p2],[tw3,p3],…},之后用户将陷门集合Tw及服务费发送至智能合约。由于智能合约在验证检索结果时可能需要数据所有者进行仲裁,用户在发送的服务费需要包含一部分仲裁费用。当仲裁费用不足时,合约的验证功能会受到一定的影响。2) After performing the above operations on each keyword to be retrieved, the trapdoor set Tw={[tw 1 ,p 1 ],[tw 2 ,p 2 ],[tw 3 ,p 3 ],…} is obtained, and then the user will The trapdoor collection Tw and the service fee are sent to the smart contract. Since the smart contract may require the data owner to arbitrate when verifying the retrieval result, the service fee sent by the user needs to include a part of the arbitration fee. When the arbitration fee is insufficient, the verification function of the contract will be affected to a certain extent.
分发算法:Distribute(Tw)→({TS1,TS2,TS3,…})。Distribution algorithm: Distribute(Tw)→({TS 1 ,TS 2 ,TS 3 ,…}).
用户将陷门及服务费发送至智能合约,智能合约执行Distribute()算法分解检索任务,并将子任务发送至各个搜索服务器节点,对应于图2中步骤④。该算法的执行过程如下:The user sends the trapdoor and service fee to the smart contract, and the smart contract executes the Distribute() algorithm to decompose the retrieval task, and sends the subtasks to each search server node, corresponding to step ④ in Figure 2. The execution of the algorithm is as follows:
1)合约账户收到用户发送的陷门集合和服务费之后的时间t内,参与检索的搜索服务器将押金发送至合约账户。合约账户收到押金后将在时间t内成功支付押金的搜索服务器按支付顺序排序,向这些服务器分发用户陷门,超时的支付押金的交易将被退回原账户。最后得到参与检索的搜索服务器集合S。1) Within time t after the contract account receives the trapdoor set and service fee sent by the user, the search server participating in the retrieval sends the deposit to the contract account. After the contract account receives the deposit, the search servers that successfully paid the deposit within time t will be sorted in the order of payment, and user trapdoors will be distributed to these servers, and the overtime deposit payment transaction will be returned to the original account. Finally, a set S of search servers participating in the retrieval is obtained.
2)为保证检索结果的可靠性,每个陷门都要由2台或以上数量的搜索服务器检索;以2台搜索服务器为例,智能合约利用搜索服务器集合S和收到的检索陷门Tw执行如下算法Algorithm 1,其中n代表云服务器数量,m代表Tw中陷门数量,TSi表示云服务器Si收到的陷门集合, 2) In order to ensure the reliability of the retrieval results, each trapdoor must be retrieved by two or more search servers; taking two search servers as an example, the smart contract uses the search server set S and the received retrieval trapdoor Tw. Execute the following algorithm Algorithm 1, where n represents the number of cloud servers, m represents the number of trapdoors in Tw, TS i represents the set of trapdoors received by cloud server Si ,
智能合约执行完毕后,将TSi分发给对应的搜索服务器。After the smart contract is executed, TS i is distributed to the corresponding search server.
检索算法:Search(TSi,I,Pu)→(RSi,R_TSi)。Retrieval algorithm: Search(TS i ,I,P u )→(RS i ,R_TS i ).
搜索服务器收到智能合约发送的检索任务后执行Search()算法,将算法执行的结果发送给智能合约及用户,对应于图2中步骤⑤。该算法的执行过程如下:The search server executes the Search() algorithm after receiving the retrieval task sent by the smart contract, and sends the result of the algorithm execution to the smart contract and the user, corresponding to step ⑤ in Figure 2. The execution of the algorithm is as follows:
1)各搜索服务器收到智能合约发送的陷门集合TSi后,对集合中每个陷门执行本地检索,得到检索结果集合RSi={Nw1,Nw2,…,Nwj,j∈(1,m)},j代表陷门编号,Nwj代表编号为j的陷门的检索结果。1) After each search server receives the trapdoor set TS i sent by the smart contract, it performs local retrieval on each trapdoor in the set, and obtains the retrieval result set RS i ={Nw 1 ,Nw 2 ,...,Nw j ,j∈ (1,m)}, j represents the trapdoor number, Nw j represents the retrieval result of the trapdoor number j.
2)搜索服务器执行本地检索时对于每个陷门利用本地存储的索引Iw’=[Cw’,Nw’],计算等式t1’·Cw’=t2’是否成立,若成立则输出1,将对应的Nw’加入集合RSi中。若不成立则输出0,将0加入集合RSi中,表明该陷门对应的检索结果为空。2) For each trapdoor when the search server performs local retrieval Using the locally stored index Iw'=[Cw', Nw'], calculate whether the equation t1'·Cw'=t2' holds, if so, output 1, and add the corresponding Nw' to the set RS i . If not, output 0 and add 0 to the set RS i , indicating that the retrieval result corresponding to the trapdoor is empty.
3)搜索服务器将检索结果集合RSi发送至智能合约用于验证。若集合RSi中检索结果均为0,则表明本次检索结果为空,检索流程结束。若集合RSi中检索结果中存在非0结果,则继续进行计算。3) The search server sends the retrieval result set RS i to the smart contract for verification. If the retrieval results in the set RS i are all 0, it indicates that the retrieval results are empty this time, and the retrieval process ends. If there is a non-zero result in the retrieval results in the set RS i , the calculation is continued.
4)对于陷门集合TSi,对应包含该集合中所有关键字的检索结果为R_TSi=Nw1&Nw2&…&Nwj。参与检索的服务器首先计算R_TSi,若R_TSi>0,表明检索结果不为空,则将检索结果R_TSi发送给用户。若R_TSi=0,则按照关键字权重计算陷门TSi的子集的检索结果的权重,将权重最大的结果R_SubTSi作为模糊结果返回给用户。R_SubTSi的计算过程如下Algorithm 2和Algorithm 3所示。4) For the trapdoor set TS i , the retrieval result corresponding to all the keywords in the set is R_TS i =Nw 1 &Nw 2 &...&Nw j . The server participating in the retrieval first calculates R_TS i , and if R_TS i >0, it indicates that the retrieval result is not empty, and sends the retrieval result R_TS i to the user. If R_TS i =0, the weight of the retrieval result of the subset of trapdoor TS i is calculated according to the keyword weight, and the result R_SubTS i with the largest weight is returned to the user as a fuzzy result. The calculation process of R_SubTS i is shown in
验证算法:Verify(RSi)→{0,1}。Verification algorithm: Verify(RS i )→{0,1}.
智能合约执行Verify()算法对搜索服务器发送的检索结果RSi进行交叉验证,对应于图2中步骤⑥。该算法的执行过程如下:The smart contract executes the Verify() algorithm to cross-verify the retrieval result RS i sent by the search server, which corresponds to step ⑥ in Figure 2. The execution of the algorithm is as follows:
1)假设2台搜索服务器对某一关键字的检索结果为Nwi与Nwi’,智能合约验证Nwi=Nwi’是否成立,即每个编号相同的陷门对应的检索结果是否相同,若成立则输出1。如果不成立则输出0,并向数据所有者发起仲裁请求,请求中包含Nwi与Nwi’。所有结果验证通过后,智能合约退回各个搜索服务器的押金,并按照检索的陷门数量向搜索服务器分发服务费。若验证失败,智能合约保留押金并拒绝支付对应搜索服务器的服务费。1) Assuming that the retrieval results of two search servers for a certain keyword are Nwi and Nwi ', the smart contract verifies whether Nwi = Nwi ' holds, that is, whether the retrieval results corresponding to each trapdoor with the same number are the same, If true, output 1. If not established, output 0, and initiate an arbitration request to the data owner, and the request includes Nwi and Nwi '. After all the results are verified, the smart contract returns the deposit of each search server, and distributes the service fee to the search server according to the number of trapdoors retrieved. If the verification fails, the smart contract retains the deposit and refuses to pay the service fee of the corresponding search server.
2)智能合约验证完成后将验证结果发送至用户,同时发起一笔交易将押金退回给搜索服务器。经过时间t后,再将服务费发送给搜索服务器。在时间t内,若用户对检索结果有怀疑可向数据所有者发起仲裁请求,该笔支付服务费的交易将被暂停。2) After the verification of the smart contract is completed, the verification result is sent to the user, and a transaction is initiated to return the deposit to the search server. After the elapse of time t, the service fee is sent to the search server. Within time t, if the user has doubts about the retrieval result, he can initiate an arbitration request to the data owner, and the transaction for paying the service fee will be suspended.
解密算法:Dec(R_TSi,PDO,Key)→M。Decryption algorithm: Dec(R_TS i ,P DO ,Key)→M.
用户收到搜索服务器发送的检索结果后,需要执行Dec()算法得到对应的明文文件,对应于图2中步骤⑦。该算法的执行过程如下:After the user receives the retrieval result sent by the search server, the user needs to execute the Dec() algorithm to obtain the corresponding plaintext file, which corresponds to step ⑦ in Figure 2. The execution of the algorithm is as follows:
1)参与检索的搜索服务器为n个时,用户收到n个检索结果{R_TS1,R_TS2,R_TS3,…,R_TSn},检索结果代表包含相应关键字的密文文件编号集合。将检索结果求交集即可得到R_Tw’,R_Tw’=R_TS1&R_TS2&R_TS3&…&R_TSn。1) When there are n search servers participating in the retrieval, the user receives n retrieval results {R_TS 1 , R_TS 2 , R_TS 3 ,..., R_TS n }, and the retrieval results represent the set of ciphertext file numbers containing the corresponding keywords. R_Tw' can be obtained by taking the intersection of the retrieval results, R_Tw'=R_TS 1 &R_TS 2 &R_TS 3 &...&R_TS n .
用户计算b=F(Key),然后将R_Tw’的第b个比特位删除,得到最终的结果R_Tw。用户将结果R_Tw发送至存储服务器请求对应的文件。存储服务器从R_Tw按比特位拆分出文件编号,查找到对应的文件后将其发送给用户。The user calculates b=F(Key), and then deletes the bth bit of R_Tw' to obtain the final result R_Tw. The user sends the result R_Tw to the storage server to request the corresponding file. The storage server splits the file number from the R_Tw bit by bit, finds the corresponding file, and sends it to the user.
2)用户获取密文文件C后首先计算得到对称密钥之后执行对称解密算法即可获取对应的明文文件M=Dec(C,k)。根据密文文件C还可以计算H4(C)’并将其与区块链中存储的H4(C)进行比较,从而判断密文文件是否被篡改。2) After the user obtains the ciphertext file C, first calculate the symmetric key Then, the symmetric decryption algorithm is executed to obtain the corresponding plaintext file M=Dec(C,k). According to the ciphertext file C, H 4 (C)' can also be calculated and compared with the H 4 (C) stored in the blockchain, so as to determine whether the ciphertext file has been tampered with.
以上为正常解密流程。此外,用户还可以对检索结果进行进一步的逻辑运算。例如,当检索关键字为{a,b,c,d},检索结果r=ra&rb&rc&rd,可计算包含关键字a,b,d的同时不含关键字c的结果r’=(r)&(!rc)。这些逻辑运算条件也可包含在检索请求中。The above is the normal decryption process. In addition, users can also perform further logical operations on the retrieval results. For example, when the search key is {a,b,c,d} and the search result r=ra&rb&rc&rd, the result r'=(r)&( !rc). These logical operation conditions can also be included in the retrieval request.
如果计算检索结果R_Tw时出现R_Tw=0的情况,此时表明不存在同时包含所有关键字的文件,可将n个检索结果中权重最大的结果作为模糊结果,也可根据需要进一步在此基础上利用区块链中的单关键字检索结果RSi进行逻辑运算,计算相应的检索结果。If R_Tw=0 occurs when the retrieval result R_Tw is calculated, it means that there is no file containing all keywords at the same time, and the result with the largest weight among the n retrieval results can be taken as the fuzzy result, or it can be further based on this as needed Use the single-keyword search result RS i in the blockchain to perform logical operations to calculate the corresponding search results.
仲裁算法:Arbitrate(w”,Nw”,x)→{0,1}。Arbitration algorithm: Arbitrate(w",Nw",x)→{0,1}.
数据所有者执行Arbitrate()算法处理由智能合约或用户发起的仲裁请求,对应于图2中步骤⑧。该算法的执行过程如下:The data owner executes the Arbitrate() algorithm to process the arbitration request initiated by the smart contract or the user, corresponding to step ⑧ in Figure 2. The execution of the algorithm is as follows:
1)对于来自智能合约的仲裁请求,数据所有者利用待仲裁的检索结果Nw”,计算H4(Nw”||x)∈VRs是否成立。若成立则输出1,表明检索结果合法。否则输出0,表明检索结果不合法,此时智能合约扣留押金并拒绝向搜索服务器支付服务费。1) For the arbitration request from the smart contract, the data owner uses the retrieval result Nw” to be arbitrated to calculate whether H 4 (Nw”||x)∈VRs is established. If established, output 1, indicating that the search result is valid. Otherwise, 0 is output, indicating that the retrieval result is invalid. At this time, the smart contract withholds the deposit and refuses to pay the service fee to the search server.
2)对于来自用户的仲裁请求,数据所有者利用待仲裁的检索结果Nw”和用户提交的原始关键字w”计算H4(w”||Nw”||x)∈VRu是否成立。若成立则输出1,表明检索结果准确。否则输出0,表明检索结果不准确。数据所有者将对应搜索服务器的信息广播至区块链中,智能合约不再向该服务器支付服务费。2) For the arbitration request from the user, the data owner uses the retrieval result Nw” to be arbitrated and the original keyword w” submitted by the user to calculate whether H 4 (w”||Nw”||x)∈VRu is established. If established, output 1, indicating that the retrieval result is accurate. Otherwise, output 0, indicating that the retrieval result is inaccurate. The data owner broadcasts the information corresponding to the search server to the blockchain, and the smart contract no longer pays the service fee to the server.
本申请在可搜索加密中引入区块链技术,提出了基于区块链的多关键字可搜索加密方法。通过方法中设计的分发算法和检索算法,使得多个搜索服务器同时参与检索过程,实现多关键字检索,降低了对单一的云服务器节点的依赖。This application introduces blockchain technology into searchable encryption, and proposes a multi-keyword searchable encryption method based on blockchain. Through the distribution algorithm and retrieval algorithm designed in the method, multiple search servers participate in the retrieval process at the same time, multi-keyword retrieval is realized, and the dependence on a single cloud server node is reduced.
从安全性方面将本申请与文献1[Xu P,Tang S,Xu P,et al.Practical multi-keyword and boolean search over encrypted e-mail in cloud server[J].IEEETransactions on Services Computing,2019,14(6):1877-1889.]以及文献2[Yang X,Chen G,Wang M,et al.Multi-keyword certificateless searchable public keyauthenticated encryption scheme based on blockchain[J].IEEE Access,2020,8:158765-158777]的方案进行了对比,如表1所示。In terms of security, this application is compared with Document 1 [Xu P, Tang S, Xu P, et al. Practical multi-keyword and boolean search over encrypted e-mail in cloud server [J]. IEEE Transactions on Services Computing, 2019, 14 (6): 1877-1889.] and document 2 [Yang X, Chen G, Wang M, et al. Multi-keyword certificateless searchable public key authenticated encryption scheme based on blockchain [J]. IEEE Access, 2020, 8: 158765- 158777] were compared, as shown in Table 1.
本申请与文献[1]、文献[2]都基于双线性配对构造了非对称可搜索加密方案,并实现了多关键字检索。本申请与文献[2]的方案均引入了区块链,同时利用智能合约实现了对检索结果的验证,保证了交易公平。两种方案都能够保证陷门的不可区分性安全,抵御内部和外部用户的关键字猜测攻击。文献[2]的方案将索引存储在区块链中,而由于区块链中的数据是透明的,索引存在一定的安全风险。本申请在运行过程中只需要在区块链中公开陷门,安全性更强。This application and the literature [1] and literature [2] both construct an asymmetric searchable encryption scheme based on bilinear pairing, and realize multi-keyword retrieval. The solutions of this application and document [2] both introduce blockchain, and at the same time use smart contracts to verify the retrieval results and ensure fair transactions. Both schemes can guarantee the indistinguishability of trapdoor security against keyword guessing attacks by internal and external users. The scheme of literature [2] stores the index in the blockchain, and because the data in the blockchain is transparent, the index has certain security risks. This application only needs to disclose the trapdoor in the blockchain during the running process, which is more secure.
而文献[1]的方案基于传统的云服务器架构,该方案只包含了用户与云服务器之间的交互过程。该方案基于诚实的云服务器模型构建,缺少可信方对检索结果的验证,无法保证交易公平,也不能抵御内部关键字猜测攻击。The solution in [1] is based on the traditional cloud server architecture, which only includes the interaction process between the user and the cloud server. The scheme is constructed based on an honest cloud server model, lacks the verification of the retrieval results by trusted parties, cannot guarantee fair transactions, and cannot defend against internal keyword guessing attacks.
表1安全性对比Table 1 Safety comparison
从计算量方面将本申请与文献[1][2]的方案进行了对比,分析了各个算法在索引构建阶段、陷门生成阶段和检索阶段的计算量,如表2所示。From the aspect of calculation amount, this application is compared with the schemes of literature [1] [2], and the calculation amount of each algorithm in the index construction stage, trapdoor generation stage and retrieval stage is analyzed, as shown in Table 2.
n表示明文文件的数量,m表示关键字的数量,k表示查询中的关键字数量,r表示查询结果对应的文件的数量(r<<n)。n represents the number of plaintext files, m represents the number of keywords, k represents the number of keywords in the query, and r represents the number of files corresponding to the query result (r<<n).
TM表示一个乘法运算的计算量,TH表示一个哈希运算的计算量,TE表示一次幂运算的计算量,TP表示一次双线性配对运算的计算量,其中TH<TM<TE<TP。T M represents the computation amount of a multiplication operation, TH represents the computation amount of a hash operation, TE represents the computation amount of an exponentiation operation, and T P represents the computation amount of a bilinear pairing operation, where T H < T M <T E <T P .
在索引构建阶段,由于索引结构的不同,文献[1]的方案的计算量主要受到文件数量的影响。本申请和文献[2]的方案受到关键字数量的影响较大,计算量相近。In the index construction stage, due to the difference in index structure, the calculation amount of the scheme in [1] is mainly affected by the number of files. The schemes of the present application and document [2] are greatly affected by the number of keywords, and the calculation amount is similar.
在陷门生成阶段,本申请和文献[1][2]的方案都与检索的关键字数量相关,文献[2]使用幂运算最少,计算量最小。本申请在此阶段涉及双线性配对运算,计算量最多。In the trapdoor generation stage, the solutions of this application and literature [1][2] are related to the number of keywords to be retrieved, and literature [2] uses the least exponentiation operation and the least amount of calculation. The present application involves bilinear pairing operations at this stage, which is the most computationally intensive.
在检索阶段,文献[1]的方案受到关键字数量和文件数量的影响,计算量最高。文献[2]不受其他参数的影响,计算量最小。本申请的计算量适中。In the retrieval stage, the scheme of the literature [1] is affected by the number of keywords and the number of documents, and the amount of computation is the highest. Reference [2] is not affected by other parameters, and the calculation amount is minimal. The amount of computation for this application is moderate.
综上,本申请在以上三个阶段的总计算量适中,但本申请在保证安全的同时灵活性更强。To sum up, the total calculation amount of the application in the above three stages is moderate, but the application is more flexible while ensuring security.
表2计算量对比Table 2 Comparison of calculation amount
实验分析:experiment analysis:
通过搭建实验环境对本申请的执行效率进行了分析。实验环境为64位Windows10操作系统,CPU为AMD Ryzen7 4800H 2.90GHz,内存16GB。实验在本地虚拟机VMwareUbuntu16.04虚拟机中进行,编程语言为python,版本为python 3.5。The execution efficiency of this application is analyzed by building an experimental environment. The experimental environment is 64-
使用SHA256算法作为本申请中的哈希函数,使用AES对称加密算法加密明文文件。本文使用的数据集为公开的Enron Email数据集,在实验中选取了其中3000个文件作为原始明文文档,并提取了其中1200个关键字用于实验分析。将本申请与文献[1][2]中的方案,在索引构建、陷门生成、搜索三个阶段的耗时进行了对比。实验过程中关键字数量从200递增至1200,步长为200。每次实验均重复50次并取平均值作为实验结果。The SHA256 algorithm is used as the hash function in this application, and the plaintext file is encrypted using the AES symmetric encryption algorithm. The dataset used in this paper is the public Enron Email dataset. In the experiment, 3000 files were selected as original plaintext documents, and 1200 keywords were extracted for experimental analysis. The time-consuming of the three stages of index construction, trapdoor generation, and search is compared with the solutions in the literature [1][2]. During the experiment, the number of keywords was increased from 200 to 1200 with a step size of 200. Each experiment was repeated 50 times and the average value was taken as the experimental result.
在索引构建阶段的耗时如下图3所示。横坐标为关键字数量,纵坐标表示基于对应数量的关键字为3000个明文文档计算索引的耗时。文献[1]的方案在索引构建阶段主要受到文件数量的影响,几乎不受到关键字数量的影响。本申请与文献[2]的方案在这一阶段的耗时相近,如图3所示。The time-consuming in the index building phase is shown in Figure 3 below. The abscissa represents the number of keywords, and the ordinate represents the time-consuming index calculation for 3000 plaintext documents based on the corresponding number of keywords. The scheme of [1] is mainly affected by the number of documents in the index construction stage, and is hardly affected by the number of keywords. The time-consuming of the solution in this application and the document [2] is similar at this stage, as shown in Figure 3.
在陷门生成阶段的耗时如图4所示。横坐标为关键字数量,纵坐标表示计算对应数量关键字的检索陷门所消耗的时间。三种方案均受到关键字数量的影响。文献[2]涉及的计算量最小,耗时最低。本方案与文献[1]的方案在此阶段的耗时相近,但由于本方案涉及双线性对运算,当关键字数量较多时耗时略高于文献[1]的方案。The time-consuming in the trapdoor generation stage is shown in Figure 4. The abscissa represents the number of keywords, and the ordinate represents the time consumed to calculate the retrieval trapdoor of the corresponding number of keywords. All three scenarios are affected by the number of keywords. Reference [2] involves the least amount of computation and the least time-consuming. The time consumption of this scheme is similar to that of the document [1] at this stage, but because this scheme involves bilinear pairing operations, the time consumption is slightly higher than that of the document [1] when the number of keywords is large.
在检索阶段的耗时如图5所示,横坐标为检索请求中包含的关键字数量,纵坐标为完成对应检索请求的耗时。由于本申请支持使用多个搜索服务器执行检索过程,在图5中分别给出了本申请在S_Search=1和S_Search=4的情况下的耗时。其中S_Search表示云服务器。本方案与文献[1]的方案的耗时与关键字数量线性相关。文献[1]的耗时几乎不受关键字数量的影响。与文献[1][2]的方案相比,本方案在此阶段的耗时适中。The time-consuming in the retrieval stage is shown in Figure 5, the abscissa is the number of keywords contained in the retrieval request, and the ordinate is the time-consuming to complete the corresponding retrieval request. Since the present application supports the use of multiple search servers to perform the retrieval process, the time consumption of the present application in the case of S_Search=1 and S_Search=4 is respectively given in FIG. 5 . Where S_Search represents the cloud server. The time-consuming of this scheme and the scheme of literature [1] is linearly related to the number of keywords. The time-consuming of literature [1] is hardly affected by the number of keywords. Compared with the schemes of literature [1][2], the time-consuming of this scheme is moderate at this stage.
最后,测试了搜索服务器数量对本方案的总耗时的影响,如下图6所示。总耗时统计了在200个关键字和3000个明文文档数量的情况下,本申请在索引构建阶段、陷门生成阶段和检索阶段的总时间。每次检索均随机选取20个关键字构建检索陷门并分发给参与检索的搜索服务器。可以看出,通过提高搜索服务器的数量可以提高本申请的运行效率。Finally, the influence of the number of search servers on the total time-consuming of this scheme is tested, as shown in Figure 6 below. The total time spent counts the total time spent in the index construction stage, trapdoor generation stage and retrieval stage of the present application under the condition of 200 keywords and 3000 plaintext documents. In each retrieval, 20 keywords were randomly selected to construct retrieval trapdoors and distributed to the search servers participating in retrieval. It can be seen that the operation efficiency of the present application can be improved by increasing the number of search servers.
本申请提出了基于区块链的多关键字可搜索加密方法,该申请将密文数据存储在存储服务器中,将索引存储在搜索服务器中。在此基础上设计了多关键字任务分发算法和检索算法,使得多个搜索服务器同时参与方法运行,提高了方法的去中心化程度。设计了仲裁机制和基于智能合约的验证机制,能够防范云服务器的恶意行为,保证用户与云服务器之间的交易公平。同时还设计了关键字权重机制,能够在多关键字检索结果为空时返回模糊结果给用户,具有更高的灵活性。通过实验分析,证明了本方法具有较高的效率。This application proposes a blockchain-based multi-keyword searchable encryption method, which stores ciphertext data in a storage server and an index in a search server. On this basis, the multi-keyword task distribution algorithm and retrieval algorithm are designed, so that multiple search servers participate in the method operation at the same time, which improves the decentralization degree of the method. An arbitration mechanism and a verification mechanism based on smart contracts are designed to prevent malicious behavior of cloud servers and ensure fair transactions between users and cloud servers. At the same time, a keyword weight mechanism is also designed, which can return fuzzy results to users when the multi-keyword search results are empty, with higher flexibility. Through experimental analysis, it is proved that this method has high efficiency.
Claims (9)
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202210355792.9A CN114741711B (en) | 2022-04-06 | 2022-04-06 | Multi-keyword searchable encryption method based on block chain |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN202210355792.9A CN114741711B (en) | 2022-04-06 | 2022-04-06 | Multi-keyword searchable encryption method based on block chain |
Publications (2)
| Publication Number | Publication Date |
|---|---|
| CN114741711A true CN114741711A (en) | 2022-07-12 |
| CN114741711B CN114741711B (en) | 2024-07-16 |
Family
ID=82280044
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN202210355792.9A Active CN114741711B (en) | 2022-04-06 | 2022-04-06 | Multi-keyword searchable encryption method based on block chain |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN114741711B (en) |
Cited By (1)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN115001715A (en) * | 2022-08-02 | 2022-09-02 | 药融云数字科技(成都)有限公司 | Encrypted intelligent contract detection method based on block chain and terminal |
Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN110599147A (en) * | 2019-09-17 | 2019-12-20 | 福州大学 | Ciphertext retrieval fair payment method and system based on block chain |
| WO2020133032A1 (en) * | 2018-12-27 | 2020-07-02 | 深圳技术大学(筹) | Multi-user ciphertext search method capable of preventing forgery |
| CN112861172A (en) * | 2021-01-26 | 2021-05-28 | 石家庄铁道大学 | Symmetric searchable encryption method based on PBFT (public domain representation) consensus mechanism |
| CN114021196A (en) * | 2021-11-18 | 2022-02-08 | 贵州大学 | Fair searchable encryption method and system |
-
2022
- 2022-04-06 CN CN202210355792.9A patent/CN114741711B/en active Active
Patent Citations (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| WO2020133032A1 (en) * | 2018-12-27 | 2020-07-02 | 深圳技术大学(筹) | Multi-user ciphertext search method capable of preventing forgery |
| CN110599147A (en) * | 2019-09-17 | 2019-12-20 | 福州大学 | Ciphertext retrieval fair payment method and system based on block chain |
| CN112861172A (en) * | 2021-01-26 | 2021-05-28 | 石家庄铁道大学 | Symmetric searchable encryption method based on PBFT (public domain representation) consensus mechanism |
| CN114021196A (en) * | 2021-11-18 | 2022-02-08 | 贵州大学 | Fair searchable encryption method and system |
Non-Patent Citations (1)
| Title |
|---|
| 闫玺玺;原笑含;汤永利;陈艳丽;: "基于区块链且支持验证的属性基搜索加密方案", 通信学报, no. 02, 29 February 2020 (2020-02-29) * |
Cited By (2)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN115001715A (en) * | 2022-08-02 | 2022-09-02 | 药融云数字科技(成都)有限公司 | Encrypted intelligent contract detection method based on block chain and terminal |
| CN115001715B (en) * | 2022-08-02 | 2022-10-21 | 药融云数字科技(成都)有限公司 | Intelligent encryption contract detection method based on block chain and terminal |
Also Published As
| Publication number | Publication date |
|---|---|
| CN114741711B (en) | 2024-07-16 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| WO2022007889A1 (en) | Searchable encrypted data sharing method and system based on blockchain and homomorphic encryption | |
| CN109981641B (en) | Block chain technology-based safe publishing and subscribing system and publishing and subscribing method | |
| Cui et al. | SVkNN: Efficient secure and verifiable k-nearest neighbor query on the cloud platform | |
| Wang et al. | Privacy-preserving public auditing for data storage security in cloud computing | |
| Li et al. | A searchable symmetric encryption scheme using blockchain | |
| CN106776904B (en) | The fuzzy query encryption method of dynamic authentication is supported in a kind of insincere cloud computing environment | |
| Yang et al. | Blockchain-based verifiable multi-keyword ranked search on encrypted cloud with fair payment | |
| Jayapandian et al. | Secure and efficient online data storage and sharing over cloud environment using probabilistic with homomorphic encryption | |
| CN115834200A (en) | Blockchain-based attribute-based searchable encrypted data sharing method | |
| CN114021164B (en) | Credit system privacy protection method based on block chain | |
| CN112163854A (en) | A hierarchical blockchain-based public key searchable encryption method and system | |
| CN111314066B (en) | Block chain-based data transfer method, terminal and computer-readable storage medium | |
| CN114039785B (en) | Data encryption, decryption and processing methods, devices, equipment and storage medium | |
| Avizheh et al. | A secure event logging system for smart homes | |
| Yao et al. | SoK: A systematic study of attacks in efficient encrypted cloud data search | |
| CN112887281A (en) | Storage method and system supporting efficient audit and multi-backup ciphertext deduplication and application | |
| Hong et al. | Constructing conditional PKEET with verification mechanism for data privacy protection in intelligent systems | |
| CN114741711B (en) | Multi-keyword searchable encryption method based on block chain | |
| CN114710357A (en) | Dynamic searchable encryption method supporting block verification in editable block chain | |
| Sun et al. | Blockchain and homomorphic encryption for digital copyright protection | |
| Xu et al. | Towards efficient privacy-preserving truth discovery in crowd sensing systems | |
| KR20210127231A (en) | Energized Identity based blockchain | |
| Li et al. | Block chain based searchable symmetric encryption | |
| CN118381606B (en) | Multi-user data multi-backup searchable encryption method based on blockchain | |
| CN117993020B (en) | Search method, device and equipment for home appliance network graph based on secure multi-party computing |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| GR01 | Patent grant | ||
| GR01 | Patent grant |