Disclosure of Invention
The embodiment of the invention provides a safety protection method, a device, a system and a storage medium of an industrial host, which can realize the safety protection of the industrial host by matching a lightweight white list and prohibiting an abnormal program from running in the industrial host.
In a first aspect, an embodiment of the present invention provides a security protection method for an industrial host, which is applied to a security protection system client installed on the industrial host, and includes:
when the target software is detected to run in the industrial host, automatically scanning the data content of the executable file of the target software to generate a target file feature code;
matching a target white list from a white list library by using the target file feature codes, and acquiring a working mode corresponding to the target file feature codes from the target white list;
determining suspicious file feature codes corresponding to suspicious files of executing target software, and inquiring whether a white list matched with the suspicious file feature codes exists in a white list library or not;
and if the file does not exist, performing corresponding alarm or blocking operation on the suspicious file according to the working mode of the target software.
Optionally, the working mode includes an alarm mode and a protection mode;
the alarm mode is used for giving an alarm in real time when the abnormal program executes the protected executable file, but the abnormal program is not blocked from executing;
and the protection mode is used for giving an alarm in real time and blocking the execution of the abnormal program when the abnormal program executes the protected executable file.
Optionally, the method further includes:
if the industrial host is detected to download or start to use the new software, setting a working mode for the new software, automatically scanning the data content of the executable file of the new software, and generating a new file feature code;
and generating a new white list by using the new file feature codes and the working mode, and storing the new white list into a white list library for updating and taking effect.
Optionally, the method further includes:
when the access of the external storage equipment is detected, judging whether the external storage equipment has the access authority or not based on the unique identifier of the external storage equipment;
and if the access authority exists, matching and acquiring the device operation authority according to the unique identifier of the external storage device, and responding to the operation of the external storage device according to the device operation authority.
In a second aspect, an embodiment of the present invention further provides a security protection device for an industrial host, which is applied to a security protection system client installed on the industrial host, and includes:
the file scanning module is used for automatically scanning the data content of the executable file of the target software to generate a target file feature code when the target software is detected to run in the industrial host;
the white list matching module is used for matching a target white list from the white list library by using the target file feature codes and acquiring a working mode corresponding to the target file feature codes from the target white list;
the query module is used for determining suspicious file feature codes corresponding to suspicious files of the executed target software and querying whether a white list matched with the suspicious file feature codes exists in a white list library or not;
and the alarm module is used for carrying out corresponding alarm or blocking operation on the suspicious file according to the working mode of the target software if the suspicious file does not exist.
Optionally, the working mode includes an alarm mode and a protection mode;
the alarm mode is used for giving an alarm in real time when the abnormal program executes the protected executable file, but the abnormal program is not blocked from executing;
and the protection mode is used for giving an alarm in real time and blocking the execution of the abnormal program when the abnormal program executes the protected executable file.
In a third aspect, an embodiment of the present invention further provides an industrial host security protection system, where the system includes: the system comprises a client installed on an industrial host and a control center installed on a server;
the client is used for executing the safety protection method of the industrial host provided by the embodiment of the invention;
and the control center is used for carrying out centralized management on the plurality of industrial hosts under the networking condition.
Optionally, the industrial host security protection system includes a stand-alone version and a network version;
the industrial host safety protection system of the stand-alone version is used for carrying out safety protection on isolated industrial hosts under the isolation condition, and the system comprises: a client installed on an industrial host;
the industrial host safety protection system of the network version is used for carrying out centralized management and control on a plurality of industrial hosts under the networking condition, and the system comprises: a client installed on an industrial host and a control center installed on a server.
Optionally, the control center is configured to collect log data reported by each client for analysis, and if a network attack event is found, cut off a propagation path of the network attack event, and generate a security policy to be issued to the clients on all the industrial hosts.
In a fourth aspect, an embodiment of the present invention further provides a computer-readable storage medium, on which a computer program is stored, where the computer program, when executed by a processor, implements the method for securing an industrial host according to any embodiment of the present invention.
In the embodiment of the invention, when the client of the industrial host safety protection system detects that the target software runs in the industrial host, the client automatically scans the data content of the executable file of the target software to generate the feature code of the target file; matching a target white list from a white list library by using the target file feature codes, and acquiring a working mode corresponding to the target file feature codes from the target white list; determining suspicious file feature codes corresponding to suspicious files of executing target software, and inquiring whether a white list matched with the suspicious file feature codes exists in a white list library or not; if the operation mode does not exist, corresponding warning or blocking operation is carried out on the suspicious file according to the working mode of the target software, the problem that the industrial host is difficult to protect in the prior art is solved, and the abnormal program is forbidden to run in the industrial host by carrying out lightweight white list matching, so that the safety protection of the industrial host is realized.
Detailed Description
The present invention will be described in further detail with reference to the accompanying drawings and examples. It is to be understood that the specific embodiments described herein are merely illustrative of the invention and are not limiting of the invention. It is to be further noted that, for the convenience of description, only a part of the structure relating to the present invention is shown in the drawings, not the whole structure.
Example one
Fig. 1a is a flowchart of a security protection method for an industrial host according to a first embodiment of the present invention, where the present embodiment is applicable to perform comprehensive security protection on the industrial host, and the method can be performed by a security protection device of the industrial host, and the security protection device can be implemented by hardware and/or software and can be generally integrated in a client of a security protection system of the industrial host that provides industrial security protection services. As shown in fig. 1a, the method comprises:
step 110, when detecting that the target software runs in the industrial host, automatically scanning the data content of the executable file of the target software to generate the feature code of the target file.
In the embodiment, in order to detect whether an abnormal program exists in the industrial host where the client is located, whether software runs in the industrial host can be detected in real time, and if the running target software is captured, the executable file of the target software is formed into the unique target file feature code through full-disk automatic scanning. The file feature code does not depend on information such as a file name, a file path or an extension of the executable file, only depends on the data feature of the executable file, and changes correspondingly as long as the executable file changes.
And step 120, matching the target white list from the white list library by using the target file feature codes, and acquiring a working mode corresponding to the target file feature codes from the target white list.
In this embodiment, the white list includes preset file feature codes and operation modes of executable files allowed to run in the industrial host. After the target file feature codes are determined, the matched white list can be inquired in the white list library by using the target file feature codes, if the target white list comprising the target file feature codes is inquired, the target software is considered to be protected conventional software, a working mode corresponding to the target file feature codes needs to be acquired from the target white list, and the safety protection level of the target software is determined. And if the white list comprising the feature codes of the target file is not inquired, the target software is considered to be unprotected, and the security protection operation is not carried out on the target software.
Optionally, the working mode includes an alarm mode and a protection mode; the alarm mode is used for giving an alarm in real time when the abnormal program executes the protected executable file, but the abnormal program is not blocked from executing; and the protection mode is used for giving an alarm in real time and blocking the execution of the abnormal program when the abnormal program executes the protected executable file.
In this embodiment, the working mode of the software to be protected may be set to an alarm mode or a protection mode according to the importance. When the working mode is the alarm mode, if the protected executable file is executed by the abnormal program, the real-time alarm is carried out according to the related information of the executable file and the abnormal program, but the execution of the abnormal program is not blocked; when the working mode is the protection mode, if the protected executable file is executed by the abnormal program, the alarm is given out and the blocking is carried out at the same time, so that the abnormal program cannot run.
In this embodiment, when the system client is installed in the industrial host, software used by the industrial host is selected, an executable file of the software is automatically scanned to generate a file feature code, the file feature code is added to a white list, a corresponding working mode is set for the software, the software is added to the white list library, and the application of the white list added to the white list library is validated, as shown in fig. 1b, so that whether the software in the host is allowed to run or not is judged according to the white list in the white list library subsequently.
Step 130, determining the suspicious file feature codes corresponding to the suspicious files of the executed target software, and inquiring whether a white list matched with the suspicious file feature codes exists in a white list library.
In this embodiment, after determining that the target software is the protected software, it needs to be further verified whether the executor of the target software is an exception program. The method comprises the steps of firstly obtaining a program for executing target software as a suspicious file, scanning data content of the suspicious file to generate a suspicious file feature code, carrying out white list matching in a white list library according to the suspicious file feature code, and if the white list is matched, determining that an executor of the target software is not an abnormal program and can normally run.
And 140, if the file does not exist, performing corresponding alarm or blocking operation on the suspicious file according to the working mode of the target software.
In this embodiment, if a white list which can be matched with the file feature codes cannot be found in the white list library, the executor of the target software is considered as an abnormal program and needs to perform corresponding protection processing, and at this time, if the working mode of the target software is an alarm mode, a real-time alarm is performed according to the relevant information of the executable file and the abnormal program, but the operation of the abnormal program is not blocked; and if the working mode is the protection mode, the abnormal program operation is blocked while the alarm is carried out.
Optionally, the method may further include: if the industrial host is detected to download or start to use the new software, setting a working mode for the new software, automatically scanning the data content of the executable file of the new software, and generating a new file feature code; and generating a new white list by using the new file feature codes and the working mode, and storing the new white list into a white list library for updating and taking effect.
In this embodiment, as shown in fig. 1b, when the industrial host needs to use new software and needs to update the white list software, the additional directory or the additional file may be used to perform white list release, or the trust directory or the trust file may be set to perform complete trust and release. And when the white list is updated, the application is required to be stored in the white list library for application to take effect. The white list of the new software can be imported and generated, and can also be scanned and generated. The import generation can directly import the generated white list into the client; and scanning generation, namely generating a new file feature code by automatically scanning the data content of the executable file of the new software, and adding the working mode of the new software and the new file feature code into a new white list. The white list library supports operations of querying, importing, exporting, displaying lists and the like of the white list.
Optionally, the method may further include: when the access of the external storage device is detected, judging whether the external storage device has the access authority or not based on the unique identifier of the external storage device; and if the access authority exists, matching and acquiring the device operation authority according to the unique identifier of the external storage device, and responding to the operation of the external storage device according to the device operation authority.
In this embodiment, as shown in fig. 1c, in order to protect the industrial host more comprehensively, an access right may be set for the external storage device in advance, so as to prevent unauthorized external storage devices from introducing viruses. Therefore, when discovering that the external storage device is accessed to the industrial host, whether the device has the access authority or not can be judged according to the device identification of the device, if the device is not authorized, the device is not allowed to be accessed, if the device is determined to have the authorization, the device identification of the device is continuously used for inquiring the specific operation authority, and only the operation of the open authority is responded.
In this embodiment, besides performing access authorization on the external storage device, the network attack of "permanent blue" and its variants can be intercepted in real time by a network defense engine and a specialized tool of a "permanent blue" vulnerability built in the system. By utilizing technologies such as vulnerability analysis, flow analysis and comparison, suspicious attack blocking and the like, the prejudgment and the prevention of the permanent blue Lesox virus can be carried out without patching and closing ports for an industrial host.
In this embodiment, the industrial host security protection system protects the resource usage of the host in a full-azimuth manner in a lightweight "white list" technical manner. According to the white list strategy, the industrial host safety protection system can prohibit the operation of illegal processes, prohibit the access of illegal USB equipment through the control of the USB mobile storage peripheral based on the unique equipment identifier, simultaneously perform authority control on legal USB equipment, and can cut off the propagation and damage paths of viruses and trojans by combining safety protection measures such as vulnerability defense and network protection.
In the embodiment of the invention, when the client of the industrial host safety protection system detects that the target software runs in the industrial host, the client automatically scans the data content of the executable file of the target software to generate the feature code of the target file; matching a target white list from a white list library by using the target file feature codes, and acquiring a working mode corresponding to the target file feature codes from the target white list; determining suspicious file feature codes corresponding to suspicious files of executing target software, and inquiring whether a white list matched with the suspicious file feature codes exists in a white list library or not; if the operation mode does not exist, corresponding warning or blocking operation is carried out on the suspicious file according to the working mode of the target software, the problem that the industrial host is difficult to protect in the prior art is solved, and the abnormal program is forbidden to run in the industrial host by carrying out lightweight white list matching, so that the safety protection of the industrial host is realized.
Example two
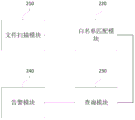
Fig. 2 is a schematic structural diagram of a security device of an industrial host according to a second embodiment of the present invention, which is applicable to a situation of performing comprehensive security protection on the industrial host, and the security device may be implemented by hardware and/or software and may be generally integrated in a client of a security protection system of the industrial host that provides an industrial security protection service. As shown in fig. 2, the apparatus includes:
the file scanning module 210 is configured to, when it is detected that target software runs in the industrial host, automatically scan data content of an executable file of the target software, and generate a target file feature code;
the white list matching module 220 is configured to match a target white list from a white list library by using the target file feature codes, and acquire a working mode corresponding to the target file feature codes from the target white list;
the query module 230 is configured to determine a suspicious file feature code corresponding to a suspicious file executing the target software, and query whether a white list matching the suspicious file feature code exists in a white list library;
and the alarm module 240 is configured to perform corresponding alarm or blocking operation on the suspicious file according to the working mode of the target software if the suspicious file does not exist.
In the embodiment of the invention, when the client of the industrial host safety protection system detects that the target software runs in the industrial host, the client automatically scans the data content of the executable file of the target software to generate the feature code of the target file; matching a target white list from a white list library by using the target file feature codes, and acquiring a working mode corresponding to the target file feature codes from the target white list; determining suspicious file feature codes corresponding to suspicious files of executing target software, and inquiring whether a white list matched with the suspicious file feature codes exists in a white list library or not; if the operation mode does not exist, corresponding warning or blocking operation is carried out on the suspicious file according to the working mode of the target software, the problem that the industrial host is difficult to protect in the prior art is solved, and the abnormal program is forbidden to run in the industrial host by carrying out lightweight white list matching, so that the safety protection of the industrial host is realized.
Optionally, the working mode includes an alarm mode and a protection mode;
the alarm mode is used for giving an alarm in real time when the abnormal program executes the protected executable file, but the abnormal program is not blocked from executing;
and the protection mode is used for giving an alarm in real time and blocking the execution of the abnormal program when the abnormal program executes the protected executable file.
Optionally, the method further includes:
the updating module is used for setting a working mode for the new software if the industrial host is detected to download or start to use the new software, automatically scanning the data content of the executable file of the new software and generating a new file feature code;
and generating a new white list by using the new file feature codes and the working mode, and storing the new white list into a white list library for updating and taking effect.
Optionally, the method further includes:
the access detection module is used for judging whether the external storage equipment has the access authority or not based on the unique identifier of the external storage equipment when the access of the external storage equipment is detected;
and if the access authority exists, matching and acquiring the device operation authority according to the unique identifier of the external storage device, and responding to the operation of the external storage device according to the device operation authority.
The safety protection device of the industrial host provided by the embodiment of the invention can execute the safety protection method of the industrial host provided by any embodiment of the invention, and has the corresponding functional modules and beneficial effects of the execution method.
EXAMPLE III
Fig. 3a is a schematic structural diagram of a safety protection system for an industrial host according to a third embodiment of the present invention, which is applicable to a situation of performing comprehensive safety protection on an industrial host. As shown in fig. 3a, the system comprises: a client 310 installed on an industrial host and a control center 320 installed on a server;
the client 310 is used for executing the safety protection method of the industrial host provided by any embodiment of the invention;
and the control center 320 is used for carrying out centralized management on the client sides on the industrial hosts under the networking condition.
In this embodiment, the client 310 is deployed on an industrial host to be protected, executes security protection operations such as white list scanning and protection, peripheral management and control, vulnerability defense, and the like, communicates with the control center, and provides related security alarm information required by the control center management.
Optionally, the control center 320 is configured to collect log data reported by each client for analysis, and if a network attack event is found, cut off a propagation path of the network attack event, generate a security policy, and issue the security policy to the clients on all industrial hosts.
In this embodiment, as shown in fig. 3B, the control center adopts a B/S architecture, which allows access through a browser anytime and anywhere to manage and control the client, and mainly includes group management, policy making and issuing, unified white list scanning (and timed scanning), client software and hardware asset management, and the like. In addition, the control center can also provide basic services of system operation and maintenance, such as: client upgrade services, data services, communication services, and the like. And the single control center can manage 6000 the plurality of host clients simultaneously and can perform security risk management based on the user organization architecture. Meanwhile, flexible module configuration, authority configuration, page configuration and scanning time configuration can be carried out aiming at each client, and the requirement of an industrial host on-site customized security strategy is met.
In this embodiment, the control center may learn the alarm information of the entire network client, grasp the entire network threat status, and preset a security protection policy, such as intercepting a common network attack event or virus. If the control center finds out a network attack event or virus and the like by analyzing the log data of the client, the control center cuts off the transmission and damage paths and issues the corresponding security protection strategy to the clients of all the hosts for security protection.
Optionally, the industrial host security protection system includes a stand-alone version and a network version; the industrial host security protection system of unit version is used for carrying out the security protection to isolated industrial host under the isolation condition, and the system includes: a client installed on an industrial host; the industrial host safety protection system of network version is used for concentrating the management and control to a plurality of industrial hosts under the networking condition, and the system includes: a client installed on an industrial host and a control center installed on a server.
In this embodiment, considering that the industrial host may not communicate with the outside due to a networking situation or other reasons, a security protection system for the industrial host in a stand-alone version and a network version is designed. The system can install a control center on the server, and for an isolated industrial host under the isolation condition, because the industrial host can not be connected with the control center, a system client installed on the industrial host can be independently regarded as an industrial host safety protection system, namely the system is switched into a single machine version, so that the safety protection of the isolated industrial host is realized. For the industrial hosts which can be networked, as the client sides on the hosts can be connected with the control center, the system can be switched into a network version, and the control center carries out security policy management, configuration issuing and the like on the client sides on all the industrial hosts in the network, so that unified management and control and security risk analysis are realized.
In this embodiment, the industrial host security protection system is a software product dedicated for industrial control environments, and by installing a client of the system on an industrial host and installing a control center of the system on a server, barrier virus interception such as entry interception, operation interception, diffusion interception and the like can be performed on the industrial host based on an intelligent matching white list technology and USB mobile storage management and control based on an equipment identifier, so that operation of malicious programs and illegal peripheral access can be prevented, comprehensive centralized management, security risk management and the like can be performed on a plurality of industrial hosts, and comprehensive security protection of the industrial host is realized.
In addition, the industrial host safety protection system can guarantee that the purchased points cannot be lost and the investment cost is additionally increased under the conditions of equipment replacement and the like through an authorization recovery mechanism aiming at the condition that the safety protection software authorization cannot be replaced and used due to the relocation of industrial equipment, the industrial replacement and the like, so that the user cost is saved.
In this embodiment, the industrial host security protection system has strong software and hardware adaptability, supports various operating systems, and various system versions such as enterprise versions and professional versions, and only requires 256M memory for hardware resources and 400M available hard disk space to adapt to more than 100 kinds of industrial software.
In the embodiment of the invention, the industrial host safety protection system comprises a client installed on the industrial host and a control center installed on a server; access authentication is carried out on external storage equipment through a client, and a malicious program in operation is intercepted by using an intelligent matching technology of a lightweight white list; the log data reported by the client side is analyzed through the control center, if a network attack event is found, the propagation path of the network attack event is cut off, a safety protection strategy is generated and issued to the client sides on all industrial hosts, the centralized management and safety risk analysis of the client sides on the industrial hosts under the networking condition are realized, the problem that the industrial hosts are difficult to protect in the prior art is solved, and the abnormal programs are forbidden to run in the industrial hosts through the light-weight white list matching, so that the safety protection of the industrial hosts is realized.
Example four
The fourth embodiment of the present invention further discloses a computer storage medium, on which a computer program is stored, where the computer program, when executed by a processor, implements a security protection method for an industrial host, and is applied to a security protection system client installed on the industrial host, and the method includes:
when the target software is detected to run in the industrial host, automatically scanning the data content of the executable file of the target software to generate a target file feature code;
matching a target white list from a white list library by using the target file feature codes, and acquiring a working mode corresponding to the target file feature codes from the target white list;
determining suspicious file feature codes corresponding to suspicious files of executing target software, and inquiring whether a white list matched with the suspicious file feature codes exists in a white list library or not;
and if the file does not exist, performing corresponding alarm or blocking operation on the suspicious file according to the working mode of the target software.
Computer storage media for embodiments of the invention may employ any combination of one or more computer-readable media. The computer readable medium may be a computer readable signal medium or a computer readable storage medium. A computer readable storage medium may be, for example, but not limited to, an electronic, magnetic, optical, electromagnetic, infrared, or semiconductor system, apparatus, or device, or any combination of the foregoing. More specific examples (a non-exhaustive list) of the computer readable storage medium would include the following: an electrical connection having one or more wires, a portable computer diskette, a hard disk, a Random Access Memory (RAM), a read-only memory (ROM), an erasable programmable read-only memory (EPROM or flash memory), an optical fiber, a portable compact disc read-only memory (CD-ROM), an optical storage device, a magnetic storage device, or any suitable combination of the foregoing. In the context of this document, a computer readable storage medium may be any tangible medium that can contain, or store a program for use by or in connection with an instruction execution system, apparatus, or device.
A computer readable signal medium may include a propagated data signal with computer readable program code embodied therein, for example, in baseband or as part of a carrier wave. Such a propagated data signal may take many forms, including, but not limited to, electro-magnetic, optical, or any suitable combination thereof. A computer readable signal medium may also be any computer readable medium that is not a computer readable storage medium and that can communicate, propagate, or transport a program for use by or in connection with an instruction execution system, apparatus, or device.
Program code embodied on a computer readable medium may be transmitted using any appropriate medium, including but not limited to wireless, wireline, optical fiber cable, RF, etc., or any suitable combination of the foregoing.
Computer program code for carrying out operations for aspects of the present invention may be written in any combination of one or more programming languages, including an object oriented programming language such as Java, Smalltalk, C + + or the like and conventional procedural programming languages, such as the "C" programming language or similar programming languages. The program code may execute entirely on the user's computer, partly on the user's computer, as a stand-alone software package, partly on the user's computer and partly on a remote computer or entirely on the remote computer or server. In the case of a remote computer, the remote computer may be connected to the user's computer through any type of network, including a Local Area Network (LAN) or a Wide Area Network (WAN), or the connection may be made to an external computer (for example, through the Internet using an Internet service provider).
It is to be noted that the foregoing is only illustrative of the preferred embodiments of the present invention and the technical principles employed. It will be understood by those skilled in the art that the present invention is not limited to the particular embodiments described herein, but is capable of various obvious changes, rearrangements and substitutions without departing from the scope of the invention. Therefore, although the present invention has been described in more detail by the above embodiments, the present invention is not limited to the above embodiments, and may include other equivalent embodiments without departing from the spirit of the present invention, and the scope of the present invention is determined by the scope of the appended claims.