CN110677396A - Security policy configuration method and device - Google Patents
Security policy configuration method and device Download PDFInfo
- Publication number
- CN110677396A CN110677396A CN201910869707.9A CN201910869707A CN110677396A CN 110677396 A CN110677396 A CN 110677396A CN 201910869707 A CN201910869707 A CN 201910869707A CN 110677396 A CN110677396 A CN 110677396A
- Authority
- CN
- China
- Prior art keywords
- address
- port number
- domain name
- session
- feature set
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Pending
Links
Images
Classifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/01—Protocols
- H04L67/02—Protocols based on web technology, e.g. hypertext transfer protocol [HTTP]
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L63/00—Network architectures or network communication protocols for network security
- H04L63/20—Network architectures or network communication protocols for network security for managing network security; network security policies in general
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L67/00—Network arrangements or protocols for supporting network services or applications
- H04L67/14—Session management
- H04L67/141—Setup of application sessions
Landscapes
- Engineering & Computer Science (AREA)
- Computer Networks & Wireless Communication (AREA)
- Signal Processing (AREA)
- Computer Security & Cryptography (AREA)
- Computer Hardware Design (AREA)
- Computing Systems (AREA)
- General Engineering & Computer Science (AREA)
- Data Exchanges In Wide-Area Networks (AREA)
- Computer And Data Communications (AREA)
Abstract
The application provides a security policy configuration method and a security policy configuration device, which are applied to network security equipment, and screen out a specific session adopting an HTTP (hyper text transport protocol) protocol by monitoring a session established between a terminal and a server; extracting an IP address, a port number and a domain name corresponding to the server in the specific session; and if the extracted IP address, the port number and the domain name are not recorded in a message feature set contained in the security policy of the server, adding the extracted IP address, the port number and the domain name to the message feature set. By the technical scheme, the message feature set contained in the security policy of the server can be automatically updated, so that the security policy is ensured to cover all Web services, and comprehensive security protection is provided for the server.
Description
Technical Field
The present application relates to the field of communications technologies, and in particular, to a security policy configuration method and apparatus.
Background
With the rapid development of network technology, the network server provides convenience for society and brings threat, and the security problem of the Web server is one of the problems. The user inputs the IP address, the domain name or the port corresponding to the Web service in the browser through the terminal equipment to carry out information communication with the Web server, and the corresponding Web server adopts an HTTP/HTTPS protocol to provide the information browsing service on the terminal network.
The network security device is generally deployed at the front end of the Web server, and configures a security policy for the corresponding Web server to provide protection for the Web service. At present, the configuration of a security policy often requires a network administrator to collect Web service information provided by a server to the outside, and then manually add a corresponding IP address, port number, and domain name to the security policy of a network security device, thereby implementing protection of the server.
Because the IP address, the domain name and the port corresponding to the Web service have diversity and variability, a network administrator manually configures a security policy for the Web service, which often cannot fully cover all the Web services, so that the Web server is easy to attack.
Disclosure of Invention
In view of this, the present application provides a security policy configuration method and apparatus, so as to automatically configure a security policy for a Web service, and comprehensively provide protection for a server.
Specifically, the method is realized through the following technical scheme:
according to a first aspect of the present application, there is provided a security policy configuration method, which is applied to a network security device, and includes:
screening out a specific session adopting an HTTP (hyper text transport protocol) protocol by monitoring a session established between a terminal and a server;
extracting an IP address, a port number and a domain name corresponding to the server in the specific session;
and if the extracted IP address, the port number and the domain name are not recorded in a message feature set contained in the security policy of the server, adding the extracted IP address, the port number and the domain name to the message feature set.
According to a second aspect of the present application, there is provided a security policy configuration apparatus, which is applied to a network security device, and includes:
the screening unit is used for screening out a specific session adopting an HTTP (hyper text transport protocol) protocol by monitoring the session established between the terminal and the server;
an extracting unit configured to extract an IP address, a port number, and a domain name corresponding to the server in the specific session;
and the adding unit is used for adding the extracted IP address, the extracted port number and the extracted domain name into the message feature set under the condition that the extracted IP address, the extracted port number and the extracted domain name are not recorded in the message feature set contained in the security policy of the server.
According to a third aspect of the present application, an electronic device is provided. The electronic device includes:
a processor;
a memory for storing processor-executable instructions;
wherein the processor implements the above security policy configuration method by executing the executable instructions.
According to a fourth aspect of the present application, there is provided a computer-readable storage medium having stored thereon a computer program which, when executed by a processor, implements the security policy configuration method described above.
Based on the technical scheme, the message feature set contained in the security policy of the server can be automatically updated in time by monitoring the session established between the terminal and the server, so that the security policy is ensured to cover all Web services, and comprehensive security protection is provided for the server.
Drawings
Fig. 1 is a schematic diagram of a network security device configuring security policies.
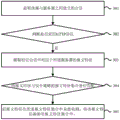
Fig. 2 is a flowchart of a security policy configuration method shown in the present application.
Fig. 3 is a flowchart illustrating a security policy configuration method according to an exemplary embodiment of the present application.
Fig. 4 is a flowchart illustrating another security policy configuration method according to an exemplary embodiment of the present application.
Fig. 5 is a schematic structural diagram of an electronic device according to an exemplary embodiment of the present application.
Fig. 6 is a block diagram illustrating a security policy configuration apparatus according to an exemplary embodiment of the present application.
Detailed Description
Reference will now be made in detail to the exemplary embodiments, examples of which are illustrated in the accompanying drawings. When the following description refers to the accompanying drawings, like numbers in different drawings represent the same or similar elements unless otherwise indicated. The embodiments described in the following exemplary embodiments do not represent all embodiments consistent with the present application. Rather, they are merely examples of apparatus and methods consistent with certain aspects of the present application, as detailed in the appended claims.
The terminology used herein is for the purpose of describing particular embodiments only and is not intended to be limiting of the application. As used in this application and the appended claims, the singular forms "a", "an", and "the" are intended to include the plural forms as well, unless the context clearly indicates otherwise. It should also be understood that the term "and/or" as used herein refers to and encompasses any and all possible combinations of one or more of the associated listed items.
It is to be understood that although the terms first, second, third, etc. may be used herein to describe various information, such information should not be limited to these terms. These terms are only used to distinguish one type of information from another. For example, first information may also be referred to as second information, and similarly, second information may also be referred to as first information, without departing from the scope of the present application. The word "if" as used herein may be interpreted as "at … …" or "when … …" or "in response to a determination", depending on the context.
Fig. 1 is a schematic diagram of a network security device configuring security policies. As shown in fig. 1, a session is established between a terminal device of a user and a server to perform information transfer, and a network security device is deployed at the front end of a network server to monitor the session established between a client and the server. The network security device in the embodiment of the application is configured with a security policy for a server, a message feature set contained in the security policy records an IP address, a port number, and a domain name corresponding to different Web services provided by the server, and the network security device can open a predefined security policy for the message feature set. The predefined security policy may be IP address interception or port interception, and the IP address, the port number, and the domain name may be collectively referred to as a packet feature. The terminal device refers to a device having an information browsing function, and may include a user device, a wireless terminal device, a mobile terminal device, and the like, for example, a mobile phone, a portable, handheld, or vehicle-mounted information browsing device, and the present application is not limited in particular.
In the process that a server provides Web services, an IP address, a port number and a domain name corresponding to the server have diversity and variability, in the related technology, a message feature set contained in a security policy in network security equipment depends on manual configuration of a network administrator, so that the message feature set contained in the security policy can not timely and comprehensively cover the Web services, and the server is easily attacked.
Therefore, the application solves the technical problems in the related art by improving the updating mode of the message feature set contained in the security policy of the server. The following examples are given for illustrative purposes.
Fig. 2 is a flowchart of a security policy configuration method shown in the present application. As shown in fig. 2, the method is applied to a network security device; may include the steps of:
In one embodiment, the network security device performs format analysis on the request message and the response message in the monitored session, so as to determine whether the session adopts the HTTP protocol. Among them, the monitored session using the HTTP protocol is referred to as a specific session.
The network security device firstly analyzes the format of the request message transmitted in the forward direction in the session and judges whether the HTTP protocol is adopted. If the request message does not meet the format content of the request message adopting the HTTP protocol, judging that the session does not adopt the HTTP protocol, and not needing to perform format analysis on the response message; if the request message meets the format content of the request message adopting the HTTP protocol, the format content of the response message is continuously analyzed. When the request message and the response message of the session are matched with the corresponding format content, the session can be determined to be a session adopting an HTTP protocol.
In another embodiment, the network security device may extract the IP address and port number in the monitored session, and perform a query in a preset detection state table, so as to determine whether the session uses the HTTP protocol.
The network security device is preset with a detection state table, which records the IP addresses and port numbers of all established sessions between the terminal and the server and whether the corresponding sessions adopt the mapping relation of the HTTP protocol. The network security device queries in the detection state table according to the monitored IP address and port number of the session, and can quickly obtain whether the session adopts an HTTP protocol. If the message is not inquired in the detection state table, format analysis is required to be performed according to the request message and the response message in the session, so as to judge whether the HTTP protocol is adopted.
And the network security equipment extracts the IP address, the port number and the domain name of the server corresponding to the session for the monitored session adopting the HTTP. The IP address, the port number, and the domain name may be collectively referred to as a packet feature.
In one embodiment, the network security device queries the extracted IP address, port number, and domain name in a message feature set included in a corresponding security policy for the server, and if the IP address, port number, and domain name of a session are queried in the message feature set, the IP address, port number, and domain name are not added to the message feature set; and if the IP address, the port number and the domain name of a certain session are not inquired in the message feature set, adding the IP address, the port number and the domain name into the message feature set.
In another embodiment, the network security device queries the extracted IP address, port number, and domain name in a preset detection result table, so as to determine whether to add the extracted IP address, port number, and domain name to the detection result table. A detection result table is preset in the network security equipment, and the mapping relation among all IP addresses, port numbers and domain names added to a message feature set contained in a security policy is recorded. If the extracted IP address, the port number and the domain name are inquired in the detection result table, the extracted IP address, the port number and the domain name are not added into the detection result table; and if the extracted IP address, the port number and the domain name are not inquired in the detection result table, adding the extracted IP address, the port number and the domain name into the detection result table. And then matching the detection result table with a message feature set contained in the security policy of the server, and adding the IP address, the port number and the domain name which are recorded in the detection result table but not recorded in the message feature set into the message feature set.
According to the technical scheme, the session established between the terminal and the server is monitored, the message characteristics of the corresponding server in the session are extracted, the message characteristic set contained in the security policy for the server can be automatically updated according to the extracted message characteristics, and the security policy of the server can cover all Web services, so that the server can obtain comprehensive protection.
For the convenience of understanding, the technical solutions of the present application are further described below with reference to the accompanying drawings. Referring to fig. 3, fig. 3 is a flowchart illustrating a security policy configuration method according to an exemplary embodiment of the present application. As shown in fig. 3, the method is applied to a network security device; may include the steps of:
And analyzing the formats of the request message and the response message in the monitored session so as to judge whether the session adopts an HTTP (hyper text transport protocol). Among them, the monitored session using the HTTP protocol is referred to as a specific session.
The network security equipment analyzes the format of the forward transmitted request message in the session so as to judge whether the HTTP is adopted. The format requirement of the request message adopting the HTTP protocol is as follows: the first line starts with a method symbol, is separated by a space, followed by the requested URI (Uniform resource identifier), is separated by a space, followed by the version number of the protocol, and finally ends with a carriage return linefeed, then repeats in the format of "name + colon (:) + space + value + carriage return linefeed", and finally ends with a carriage return linefeed as a single line.
If the request message does not meet the format content, the session is judged not to adopt an HTTP protocol, and the format analysis of the response message is not needed.
And if the request message meets the format content, continuing to perform format analysis on the response message. The format requirements of the response message adopting the HTTP protocol are as follows: the first line starts with a version of the server HTTP protocol, separated by a space, followed by a response status code sent back by the server, separated by a space, followed by a textual description of the status code, and finally ended with a carriage return line change as a single line.
And if the request message and the response message are matched with the format content of the HTTP protocol, judging that the session is a specific session adopting the HTTP protocol.
Extracting the message feature corresponding to the server in a particular session may include extracting an IP address, a port number, and a domain name corresponding to the server in a session satisfying an HTTP protocol. The IP address, port number, and domain name may be collectively referred to as a message feature.
And inquiring the extracted IP address, port number and domain name of the specific session in a message feature set contained in a security policy for the server. If the IP address, the port number and the domain name of the specific session are inquired in the message feature set, the IP address, the port number and the domain name are not added into the message feature set, and the message feature set is kept unchanged.
And if the extracted IP address, port number and domain name of the specific session are not inquired in the message feature set, adding the IP address, port number and domain name of the specific session into the message feature set to update the message feature set.
According to the technical scheme, the session established between the terminal and the server is monitored, the message characteristics of the corresponding server in the session are extracted, the message characteristic set contained in the security policy for the server can be automatically updated according to the extracted message characteristics, and the security policy of the server can cover all Web services, so that the server can obtain comprehensive protection.
Fig. 4 is a flowchart illustrating another security policy configuration method according to an exemplary embodiment of the present application. As shown in fig. 4, the method applied to the network security device may include the following steps:
And extracting the IP address and the port number of the corresponding server in the session established between the monitored terminal and the server, and judging whether the IP address and the port number are recorded in the detection state table.
A detection state table is preset in the network security device, and as shown in table 1 below, IP addresses and port numbers of all sessions established between the terminal and the server and whether the corresponding session adopts the mapping relationship of the HTTP protocol or not are recorded.
TABLE 1
| IP address | Port number | Yes/no using HTTP protocol |
| 192.168.0.1 | 80 | Is that |
| 192.168.0.2 | 8081 | Is that |
| 192.168.0.3 | 8080 | Whether or not |
| …… | …… | …… |
According to the extracted IP address and port number in the session, the query is carried out in the detection state table, and whether the session corresponding to the IP address and the port number adopts an HTTP protocol or not can be quickly obtained.
In step 403, the detection status table is queried whether to use the HTTP protocol.
If the extracted IP address and the port number are inquired in the detection state table, whether the session adopts the HTTP protocol or not can be quickly obtained directly according to the record of the detection state table. By inquiring the IP address and the port number in the detection state table, whether the session adopts the HTTP can be quickly judged, and the format analysis of the request message and the response message in the session is avoided every time.
If the session is inquired to adopt the HTTP protocol, the step 405 is carried out; if the session is inquired not to adopt the HTTP protocol, the session does not need to be processed.
If the extracted IP address and port number are not found in the detection state table, format analysis is performed on the request message and the response message in the session, and it is determined whether the session employs the HTTP protocol, which is the same as step 302, and is not repeated here, and after the determination is finished, the mapping relationship between the IP address and port number of the session and whether the HTTP protocol is employed needs to be added to the detection state table.
In step 405, the domain name in the particular session is extracted.
According to the message format in the session adopting the HTTP protocol, the request message is analyzed, the value which is the Host is extracted, the content of the value is the domain name, the IP address and the port number which correspond to the server in the specific session are extracted in the front, and the IP address, the port number and the domain name in the session meeting the HTTP protocol can be obtained.
According to the extracted IP address, port number and domain name of the corresponding server in the specific session, whether the IP address, port number and domain name are recorded in the detection result table can be judged.
A detection result table is preset in the network security device, and as shown in table 2 below, all IP addresses, port numbers, and domain names that have been added to the packet feature set of the security policy are recorded. Furthermore, as shown in table 2 below, the same IP address and port number may correspond to different domain names.
If the IP address, the port number and the domain name of the specific session are inquired in the detection result table, the detection result table is kept unchanged.
TABLE 2
| IP address | Port number | Domain name |
| 192.168.0.1 | 80 | abc01.com |
| 192.168.0.2 | 8081 | abc02.com |
| 192.168.0.2 | 8081 | abc03.com |
| …… | …… | …… |
And if the IP address, the port number and the domain name of the specific session are not inquired in the detection result table, adding the IP address, the port number and the domain name into the detection result table.
And step 408, synchronizing the message feature sets according to the detection result table.
Matching the detection result table with a message feature set contained in a security policy of the server, and if the IP address, the port number and the domain name recorded in the detection result table do not exist in the message feature set, adding the IP address, the port number and the domain name to the message feature set contained in the security policy; and if the IP address, the port number and the domain name recorded in the detection result table exist in the message feature set contained in the security policy, keeping the message feature set of the security policy unchanged. The message feature sets are synchronized through the detection result table, so that the message feature sets can be prevented from being frequently used for query matching, and the speed of security policy configuration can be prevented from being influenced.
For example, suppose that a user a logs in a network through a terminal device of the user to access a certain website, the IP address of the network security device extraction server is 192.168.0.1, and the port number is 80. Assuming that another user B logs in the network through the user terminal and accesses another website, the IP address extracted by the network security device to the server is 192.168.0.4, and the port number is 8080.
According to the table 1, it can be quickly inquired that the session established between the user A and the server has a record in the table 1, and the session corresponding to the IP address and the port number adopts an HTTP protocol; the IP address 192.168.0.4 and the port number 8080 corresponding to the session established between the user B and the server are not found in table 1, and therefore, format analysis needs to be performed on the request packet and the response packet in the session to determine whether the session adopts the HTTP protocol, assuming that the determination result is that the session adopts the HTTP protocol, and the mapping relationship between the corresponding IP address, the corresponding port number, and whether the HTTP protocol is adopted is added to table 1, and the obtained result is shown in table 3 below. In fact, whether the session adopts the HTTP protocol or not, the mapping relationship between the IP address, the port number, and whether the HTTP protocol is adopted or not of the session needs to be added to the above table 1.
TABLE 3
| IP address | Port number | Yes/no using HTTP protocol |
| 192.168.0.1 | 80 | Is that |
| 192.168.0.2 | 8081 | Is that |
| 192.168.0.3 | 8080 | Whether or not |
| …… | …… | …… |
| 192.168.0.4 | 8080 | Is that |
Next, in the session established between the user a and the server, the IP address of the server is 192.168.0.1, the port number is 80, and the domain name is abc01. com. The IP address of the server in the session established between the user B and the server is 192.168.0.4, the port number is 8080, and the domain name is abc04.com.
The query is performed according to table 2, and the IP address, the port number, and the domain name extracted in the session established between the user a and the server can be queried in table 2, so that table 2 is kept unchanged. The IP address, port number, and domain name extracted from the session established between the user B and the server are not found in table 2, and therefore, the corresponding packet characteristics are added to table 2, and the obtained results are shown in table 4 below.
TABLE 4
| IP address | Port number | Domain name |
| 192.168.0.1 | 80 | abc01.com |
| 192.168.0.2 | 8081 | abc02.com |
| 192.168.0.2 | 8081 | abc03.com |
| …… | …… | …… |
| 192.168.0.4 | 8080 | abc04.com |
And matching the content of the table 4 with a message feature set contained in the security policy, and if the IP address, the port number and the domain name recorded in the detection result table exist in the message feature set, keeping the message feature set unchanged.
According to the technical scheme, the session established between the terminal and the server is monitored, the message characteristics of the corresponding server in the session are extracted, the message characteristic set contained in the security policy for the server can be automatically updated according to the extracted message characteristics, and the security policy of the server can cover all Web services, so that the server can obtain comprehensive protection.
Fig. 5 shows a schematic structural diagram of an electronic device according to an exemplary embodiment of the present application. Referring to fig. 5, at the hardware level, the electronic device includes a processor 501, an internal bus 502, a network interface 503, a memory 504, and a non-volatile memory 505, but may also include hardware required for other services. The processor 501 reads a corresponding computer program from the non-volatile memory 505 into the memory 504 and then runs the computer program, thereby forming a security policy configuration device on a logical level. Of course, besides the software implementation, the present application does not exclude other implementations, such as logic devices or a combination of software and hardware, and the like, that is, the execution subject of the following processing flow is not limited to each logic unit, and may also be hardware or logic devices.
Referring to fig. 6, in a software embodiment, the security policy configuration apparatus may include a screening unit 601, an extracting unit 602, and an adding unit 603. Wherein:
a screening unit 601, which screens out a specific session using HTTP protocol by monitoring a session established between a terminal and a server;
an extracting unit 602, which extracts an IP address, a port number, and a domain name corresponding to the server in the specific session;
the adding unit 603 is configured to add the extracted IP address, port number, and domain name to the packet feature set when the extracted IP address, port number, and domain name are not recorded in the packet feature set included in the security policy of the server.
Optionally, the screening unit may extract an IP address and a port number corresponding to the server in any monitored session, match the extracted IP address and port number with a preset detection state table, and determine whether any session uses an HTTP protocol according to a matching result. The detection state table records the mapping relation between the IP addresses and the port numbers of all the established sessions between the terminal and the server and whether the corresponding sessions use the HTTP protocol or not.
Optionally, the screening unit may perform format analysis on a request packet and a response packet transmitted in any monitored session to determine whether the format of the request packet and the format of the response packet match an HTTP protocol packet format, and if both the request packet and the response packet match the HTTP protocol packet format, determine that the HTTP protocol is adopted by the any session.
Optionally, the method further includes:
the adding unit may match the extracted IP address, port number, and domain name of any specific session with a preset detection result table, add the IP address, port number, and domain name of any specific session to the detection result table when a matching result indicates that the detection result table does not include the IP address, port number, and domain name of any specific session, and synchronize the packet feature set according to the detection result table, so as to add the IP address, port number, and domain name of any specific session to the packet feature set. And the detection result table records the mapping relation between all IP addresses and port numbers added to the message feature set and the corresponding domain names.
Optionally, the adding unit matches the extracted IP address, port number, and domain name of any specific session with the packet feature set, and adds the IP address, port number, and domain name of any specific session to the packet feature set when a matching result indicates that the packet feature set does not include the IP address, port number, and domain name of any specific session.
The implementation process of the functions and actions of each unit in the above device is specifically described in the implementation process of the corresponding step in the above method, and is not described herein again.
For the device embodiments, since they substantially correspond to the method embodiments, reference may be made to the partial description of the method embodiments for relevant points. The above-described embodiments of the apparatus are merely illustrative, and the units described as separate parts may or may not be physically separate, and parts displayed as units may or may not be physical units, may be located in one place, or may be distributed on a plurality of network units. Some or all of the modules can be selected according to actual needs to achieve the purpose of the scheme of the application. One of ordinary skill in the art can understand and implement it without inventive effort.
In an exemplary embodiment, there is also provided a non-transitory computer-readable storage medium, such as a memory, including instructions executable by a processor of a transmitting device of a message to perform the method, which may include:
screening out a specific session adopting an HTTP (hyper text transport protocol) protocol by monitoring a session established between a terminal and a server;
extracting an IP address, a port number and a domain name corresponding to the server in the specific session;
and if the extracted IP address, the port number and the domain name are not recorded in a message feature set contained in the security policy of the server, adding the extracted IP address, the port number and the domain name to the message feature set.
Optionally, the screening out a specific session using the HTTP protocol includes: extracting the IP address and the port number corresponding to the server in any monitored session;
matching the extracted IP address and port number with a preset detection state table, wherein the detection state table records the mapping relation of the IP addresses and the port numbers of all established sessions between the terminal and the server and whether the corresponding sessions use the HTTP protocol;
and determining whether any session adopts an HTTP (hyper text transport protocol) according to the matching result.
Optionally, the screening out a specific session using the HTTP protocol includes: carrying out format analysis on the monitored request message and response message transmitted in any session so as to determine whether the format is matched with the format of the HTTP protocol message;
and if the request message and the response message are both matched with the HTTP protocol message format, judging that any session adopts an HTTP protocol.
Optionally, the method further includes:
if the extracted IP address, port number, and domain name are not recorded in a packet feature set included in the security policy of the server, adding the extracted IP address, port number, and domain name to the packet feature set includes: matching the extracted IP address, port number and domain name of any specific session with a preset detection result table, wherein the detection result table records the mapping relation between all IP addresses and port numbers added to the message feature set and corresponding domain names;
when the matching result shows that the detection result table does not contain the IP address, the port number and the domain name of any specific session, the IP address, the port number and the domain name of any specific session are added into the detection result table;
and synchronizing the message feature set according to the detection result table so as to add the IP address, the port number and the domain name of any specific session to the message feature set.
Optionally, if the extracted IP address, port number, and domain name are not recorded in a packet feature set included in the security policy of the server, adding the extracted IP address, port number, and domain name to the packet feature set includes: matching the extracted IP address, port number and domain name of any specific session with the message feature set;
and when the matching result shows that the message feature set does not contain the IP address, the port number and the domain name of any specific session, adding the IP address, the port number and the domain name of any specific session into the message feature set.
The non-transitory computer readable storage medium may be a ROM, a Random Access Memory (RAM), a CD-ROM, a magnetic tape, a floppy disk, an optical data storage device, etc., which is not limited in this application.
The above description is only exemplary of the present application and should not be taken as limiting the present application, as any modification, equivalent replacement, or improvement made within the spirit and principle of the present application should be included in the scope of protection of the present application.
Claims (12)
1. A method for configuring a security policy, comprising:
screening out a specific session adopting an HTTP (hyper text transport protocol) protocol by monitoring a session established between a terminal and a server;
extracting an IP address, a port number and a domain name corresponding to the server in the specific session;
and if the extracted IP address, the port number and the domain name are not recorded in a message feature set contained in the security policy of the server, adding the extracted IP address, the port number and the domain name to the message feature set.
2. The method of claim 1, wherein screening out specific sessions that employ the HTTP protocol comprises:
extracting the IP address and the port number corresponding to the server in any monitored session;
matching the extracted IP address and port number with a preset detection state table, wherein the detection state table records whether the IP addresses and the port numbers of all established sessions between the terminal and the server and the corresponding sessions adopt the mapping relation of an HTTP (hyper text transport protocol);
and determining whether any session adopts an HTTP (hyper text transport protocol) according to the matching result.
3. The method of claim 1, wherein screening out specific sessions that employ the HTTP protocol comprises:
carrying out format analysis on the monitored request message and response message transmitted in any session so as to determine whether the format is matched with the format of the HTTP protocol message;
and if the request message and the response message are both matched with the HTTP protocol message format, judging that any session adopts an HTTP protocol.
4. The method according to claim 1, wherein if the extracted IP address, port number, and domain name are not recorded in a packet feature set included in the security policy of the server, adding the extracted IP address, port number, and domain name to the packet feature set comprises:
matching the extracted IP address, port number and domain name of any specific session with a preset detection result table, wherein the detection result table records the mapping relation between all IP addresses and port numbers added to the message feature set and corresponding domain names;
when the matching result shows that the detection result table does not contain the IP address, the port number and the domain name of any specific session, the IP address, the port number and the domain name of any specific session are added into the detection result table;
and synchronizing the message feature set according to the detection result table so as to add the IP address, the port number and the domain name of any specific session to the message feature set.
5. The method according to claim 1, wherein if the extracted IP address, port number, and domain name are not recorded in a packet feature set included in the security policy of the server, adding the extracted IP address, port number, and domain name to the packet feature set comprises:
matching the extracted IP address, port number and domain name of any specific session with the message feature set;
and when the matching result shows that the message feature set does not contain the IP address, the port number and the domain name of any specific session, adding the IP address, the port number and the domain name of any specific session into the message feature set.
6. A security policy configuration apparatus, comprising:
the screening unit is used for screening out a specific session adopting an HTTP (hyper text transport protocol) protocol by monitoring the session established between the terminal and the server;
an extracting unit configured to extract an IP address, a port number, and a domain name corresponding to the server in the specific session;
and the adding unit is used for adding the extracted IP address, the extracted port number and the extracted domain name into the message feature set under the condition that the extracted IP address, the extracted port number and the extracted domain name are not recorded in the message feature set contained in the security policy of the server.
7. The apparatus according to claim 6, wherein the screening unit is specifically configured to:
extracting the IP address and the port number corresponding to the server in any monitored session;
matching the extracted IP address and port number with a preset detection state table, wherein the detection state table records the mapping relation of the IP addresses and the port numbers of all established sessions between the terminal and the server and whether the corresponding sessions use the HTTP protocol;
and determining whether any session adopts an HTTP (hyper text transport protocol) according to the matching result.
8. The apparatus according to claim 6, wherein the screening unit is specifically configured to:
carrying out format analysis on the monitored request message and response message transmitted in any session so as to determine whether the format is matched with the format of the HTTP protocol message;
and if the request message and the response message are both matched with the HTTP protocol message format, judging that any session adopts an HTTP protocol.
9. The apparatus according to claim 6, wherein the adding unit is specifically configured to:
matching the extracted IP address, port number and domain name of any specific session with a preset detection result table, wherein the detection result table records the mapping relation between all IP addresses and port numbers added to the message feature set and corresponding domain names;
when the matching result shows that the detection result table does not contain the IP address, the port number and the domain name of any specific session, the IP address, the port number and the domain name of any specific session are added into the detection result table;
and synchronizing the message feature set according to the detection result table so as to add the IP address, the port number and the domain name of any specific session to the message feature set.
10. The apparatus according to claim 6, wherein the adding unit is specifically configured to:
matching the extracted IP address, port number and domain name of any specific session with the message feature set;
and when the matching result shows that the message feature set does not contain the IP address, the port number and the domain name of any specific session, adding the IP address, the port number and the domain name of any specific session into the message feature set.
11. An electronic device, comprising:
a processor;
a memory for storing processor-executable instructions;
wherein the processor implements the method of any one of claims 1-5 by executing the executable instructions.
12. A computer-readable storage medium having stored thereon computer instructions, which when executed by a processor, perform the steps of the method according to any one of claims 1-5.
Priority Applications (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201910869707.9A CN110677396A (en) | 2019-09-16 | 2019-09-16 | Security policy configuration method and device |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| CN201910869707.9A CN110677396A (en) | 2019-09-16 | 2019-09-16 | Security policy configuration method and device |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| CN110677396A true CN110677396A (en) | 2020-01-10 |
Family
ID=69077013
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| CN201910869707.9A Pending CN110677396A (en) | 2019-09-16 | 2019-09-16 | Security policy configuration method and device |
Country Status (1)
| Country | Link |
|---|---|
| CN (1) | CN110677396A (en) |
Cited By (4)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN111800408A (en) * | 2020-06-30 | 2020-10-20 | 深信服科技股份有限公司 | Policy configuration device, security policy configuration method of terminal, and readable storage medium |
| CN112954027A (en) * | 2021-01-29 | 2021-06-11 | 杭州迪普科技股份有限公司 | Network service characteristic determination method and device |
| CN113422723A (en) * | 2021-05-13 | 2021-09-21 | 新华三信息安全技术有限公司 | Method and equipment for forwarding message |
| CN113992395A (en) * | 2021-10-26 | 2022-01-28 | 新华三信息安全技术有限公司 | Terminal identification method and device, electronic equipment and medium |
Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN102638580A (en) * | 2012-03-30 | 2012-08-15 | 奇智软件(北京)有限公司 | Webpage information processing method and webpage information processing device |
| CN104394122A (en) * | 2014-10-31 | 2015-03-04 | 杭州安恒信息技术有限公司 | HTTP (Hyper Text Transport Protocol) service firewall based on adaptive agent mechanism |
| WO2017001870A1 (en) * | 2015-07-02 | 2017-01-05 | Payfont Limited | Resilient secret sharing cloud based architecture for data vault |
| CN107454109A (en) * | 2017-09-22 | 2017-12-08 | 杭州安恒信息技术有限公司 | A network stealing behavior detection method based on HTTP traffic analysis |
| CN108712367A (en) * | 2018-03-28 | 2018-10-26 | 新华三信息安全技术有限公司 | A kind of message processing method, device and equipment |
| CN109525586A (en) * | 2018-11-29 | 2019-03-26 | 杭州迪普科技股份有限公司 | Security policy configuration method and device based on URL |
-
2019
- 2019-09-16 CN CN201910869707.9A patent/CN110677396A/en active Pending
Patent Citations (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN102638580A (en) * | 2012-03-30 | 2012-08-15 | 奇智软件(北京)有限公司 | Webpage information processing method and webpage information processing device |
| CN104394122A (en) * | 2014-10-31 | 2015-03-04 | 杭州安恒信息技术有限公司 | HTTP (Hyper Text Transport Protocol) service firewall based on adaptive agent mechanism |
| WO2017001870A1 (en) * | 2015-07-02 | 2017-01-05 | Payfont Limited | Resilient secret sharing cloud based architecture for data vault |
| CN107454109A (en) * | 2017-09-22 | 2017-12-08 | 杭州安恒信息技术有限公司 | A network stealing behavior detection method based on HTTP traffic analysis |
| CN108712367A (en) * | 2018-03-28 | 2018-10-26 | 新华三信息安全技术有限公司 | A kind of message processing method, device and equipment |
| CN109525586A (en) * | 2018-11-29 | 2019-03-26 | 杭州迪普科技股份有限公司 | Security policy configuration method and device based on URL |
Cited By (6)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| CN111800408A (en) * | 2020-06-30 | 2020-10-20 | 深信服科技股份有限公司 | Policy configuration device, security policy configuration method of terminal, and readable storage medium |
| CN111800408B (en) * | 2020-06-30 | 2022-09-30 | 深信服科技股份有限公司 | Policy configuration device, security policy configuration method of terminal, and readable storage medium |
| CN112954027A (en) * | 2021-01-29 | 2021-06-11 | 杭州迪普科技股份有限公司 | Network service characteristic determination method and device |
| CN113422723A (en) * | 2021-05-13 | 2021-09-21 | 新华三信息安全技术有限公司 | Method and equipment for forwarding message |
| CN113992395A (en) * | 2021-10-26 | 2022-01-28 | 新华三信息安全技术有限公司 | Terminal identification method and device, electronic equipment and medium |
| CN113992395B (en) * | 2021-10-26 | 2023-10-24 | 新华三信息安全技术有限公司 | Terminal identification method, device, electronic equipment and medium |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| CN110677396A (en) | Security policy configuration method and device | |
| CN106921637B (en) | Method and device for identifying application information in network flow | |
| US8949368B2 (en) | Method for cache object aggregation | |
| US9258289B2 (en) | Authentication of IP source addresses | |
| US20170048155A1 (en) | Protocol type identification method and apparatus | |
| CN107888605B (en) | A method and system for traffic security analysis of Internet of Things cloud platform | |
| JP2018531527A6 (en) | Method and apparatus for identifying application information in network traffic | |
| CN108259425A (en) | The determining method, apparatus and server of query-attack | |
| CN110430188B (en) | Rapid URL filtering method and device | |
| CN110399546B (en) | Link duplicate removal method, device, equipment and storage medium based on web crawler | |
| CN105635073B (en) | Access control method and device and network access equipment | |
| US11178160B2 (en) | Detecting and mitigating leaked cloud authorization keys | |
| CN114338600B (en) | Equipment fingerprint selection method and device, electronic equipment and medium | |
| CN107666404B (en) | Broadband network user identification method and device | |
| CN106104550A (en) | Site information extraction element, system, site information extracting method and site information extraction procedure | |
| CN107454007A (en) | A kind of processing method and processing device of gateway service | |
| CN105635064A (en) | CSRF attack detection method and device | |
| US11599673B2 (en) | Ascertaining network devices used with anonymous identifiers | |
| CN107592299B (en) | Proxy internet access identification method, computer device and computer readable storage medium | |
| CN113079157A (en) | Method and device for acquiring network attacker position and electronic equipment | |
| CN105450513B (en) | Method and cloud storage server for archiving email attachments | |
| CN104009999B (en) | Prevent method, device and network access server that ARP is cheated | |
| CN107332856B (en) | Address information detection method and device, storage medium and electronic device | |
| CN103916365B (en) | The method and apparatus of the network behavior feature of export and verification malicious code | |
| CN113395367A (en) | HTTPS service identification method and device, storage medium and electronic equipment |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| PB01 | Publication | ||
| PB01 | Publication | ||
| SE01 | Entry into force of request for substantive examination | ||
| SE01 | Entry into force of request for substantive examination | ||
| RJ01 | Rejection of invention patent application after publication | ||
| RJ01 | Rejection of invention patent application after publication |
Application publication date: 20200110 |