$ poetry install
You will also need ganache. If not installed yet:
$ npm install -g ganache
Do not forget to pass the network, since this project supports multiple chains:
$ brownie test --network goerli-fork
All modules have as a goal to lower the signing threshold needed to perform emergency actions on multisigs, and/or abstract away gas costs associated with such actions. Proof-of-concepts exist for arbitrary revoking ERC20 allowance, withdrawals of LP positions and the closing of lending positions on money markets:
-
RevokeModule: allows to revoke outstanding approvals for any given token and spender, as long as it is triggered by one of the owners of the safe or the Gelato relayer. -
UniswapWithdrawModule: this module allows for any signer to singlehandedly call (and execute!) a withdrawal of any Uniswap V2 lp position:uniswapV2Withdraw(lpTokenAddress). -
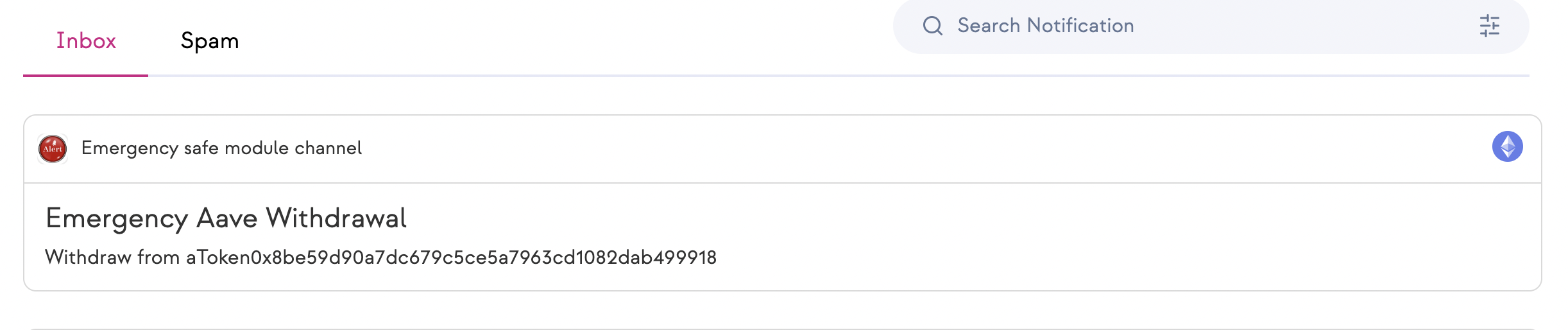
AaveWithdrawModule: allows emergency withdrawals from any V3 aToken position by letting a single signer callaaveV3Withdraw(aTokenAddress). The module will withdraw on behalf of the multisig, indiffferent of the actual signer's threshold needed by the safe (Safe.getThreshold).
Said modules can be deployed from the ModuleFactory, which takes the Safe address as its only constructor argument. Once deployed, the module needs to be enabled in a regular multisig transaction (Safe.enableModule).
We defined the concept of "guardians", which are entities working tightly together with the Safe signers in the security space. Transaction sponsors provide the "guardians" with the GELATO_API_KEY which will allow them to trigger the modules in case of an emergency.
These emergency methods are tightly scoped and can be executed with relatively low risk. Gas is prepaid, cannot be used for other purposes and is thus completely abstracted away from the guardian.
Imagine a world in which security experts such as @peckshield or @ZachXBT are appointed as a trusted guardian, and can revoke, withdraw or close positions across a collection of multisigs in case of war room situations.
Modules are hooked up automatically to a channel belonging to the Safe. This channel provides a way for signers to communicate and always stay up-to-date on when high level emergency transactions gets executed.
All these modules could be managed through a dapp. This dapp would provide a smoother experience when it comes to deploying, managing and monitoring the modules. Both deployment and enabling of the module could then be done in one transaction, which is only possible atomically due to Safe's GS031.
We experimented with deploying an ERC20 approvals subgraph to inform Safe users on their outstanding approvals. This could even enable batch revokes, in case of multiple outstanding (inifinite) approvals.
Push protocol chat and notifications could be made visible here, as could monitoring of supported positions.
-
Safe(v1.3.0+L2) -
Safe(v.1.4.0, ERC-4337 enabled!) -
ModuleFactory -
UniswapWithdrawModule -
RevokeModule -
AaveWithdrawModule
Some successful executions of these ideas on Görli to showcase these proof-of-concepts:
- Signer
0xef42callsaaveV3Withdraw(aTokenAddress)on theAaveWithdrawModuleinstalled on their Safe. The transaction does not need to reach threshold as normal; one alert signer is in this case enough to trigger the emergency withdrawal [tx hash]. - This Gelato task https://relay.gelato.digital/tasks/status/0x9c0a4ef4e2adfa31e0b97c356c8deec8e5253f15511c85c8b8a590c55bc9b903, initiated by a web2 guardian, triggering a revoke on-chain (
approve(owner, spender, 0)) on an arbitrary token and spender [tx hash]. Signers pre-approved (the scope of) the module in advance, and were not needed to sign [tx hash]. Gas was paid for in advance as well [tx hash]. - Signer
0x3f99callsuniswapV2Withdraw()on the uniswap module after enabling it. Without needing other signatures, the module withdraws the LP position into its underlying assets back to the multisig [tx hash].
- The multisig wants to swap on CoW Swap and approves the CoW Protocol Vault Relayer for 10 wxDAI [tx hash]. The gas costs for this transaction are sponsored by Gnosis, and no gas fees are paid for execution.
- Signer
0x1377callsrevoke(token, spender)on theRevokeModule. Without needing other signers, the wxDAI allowance is revoked [tx hash].
- Signer
0x1377callsrevoke(token, spender)on theRevokeModule. Without needing other signers, the WETH allowance is revoked [tx hash].
This repository was initiated at the ETHGlobal Tokyo 2023 hackathon and release v0.1 was submitted as our official submission!
どうもありがとうございます!