Helper script for identifying bad characters based on (Immunity|edb)'s stack dump
TL;DR Usage
Buffer Overflows have been officially out of OSCP as of March 15 2023
For more information, please refer to the 'PEN-200 (PWK): Updated for 2023' blog post
This repo is now archived and will no longer be maintained beyond this point
I started my PEN-200 journey not too long ago. I've always loved buffer overflows, but absolutely hated dealing with bad character identification.
I decided to change that as a way of giving back to the community, and possibly saving other members their time and hassle.
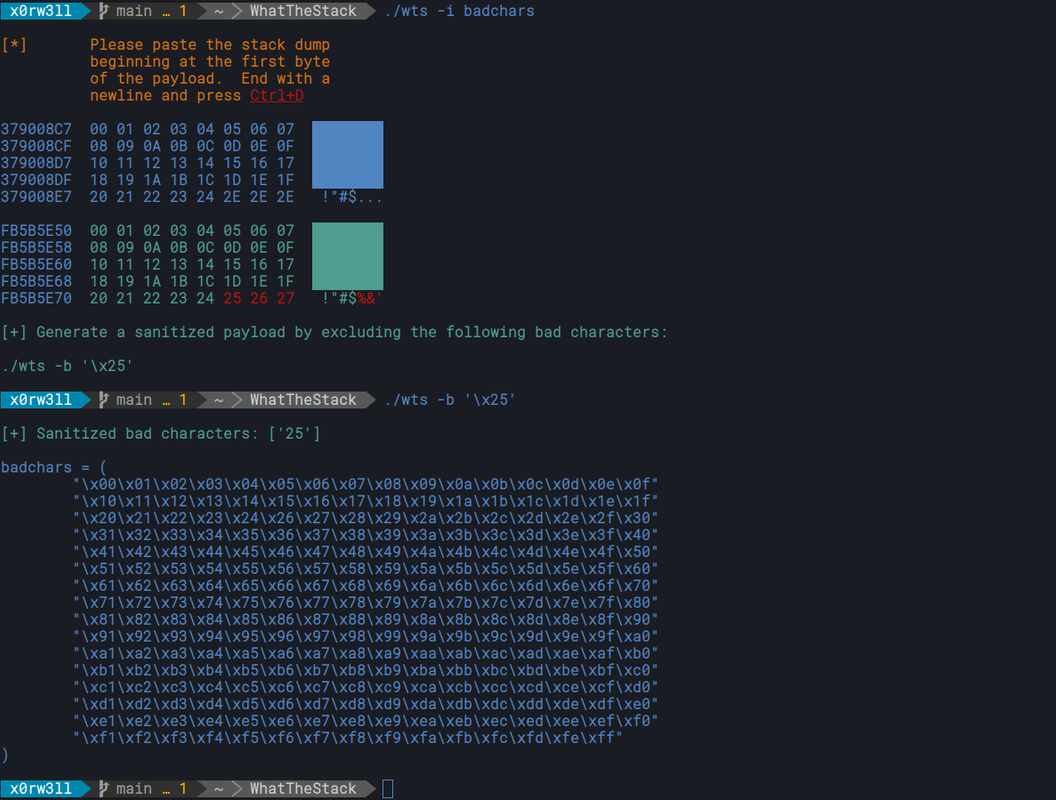
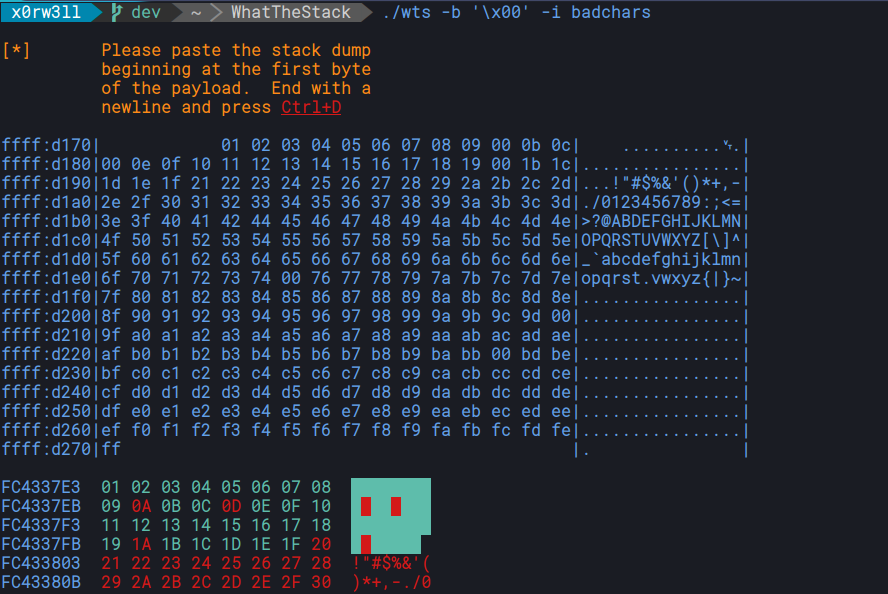
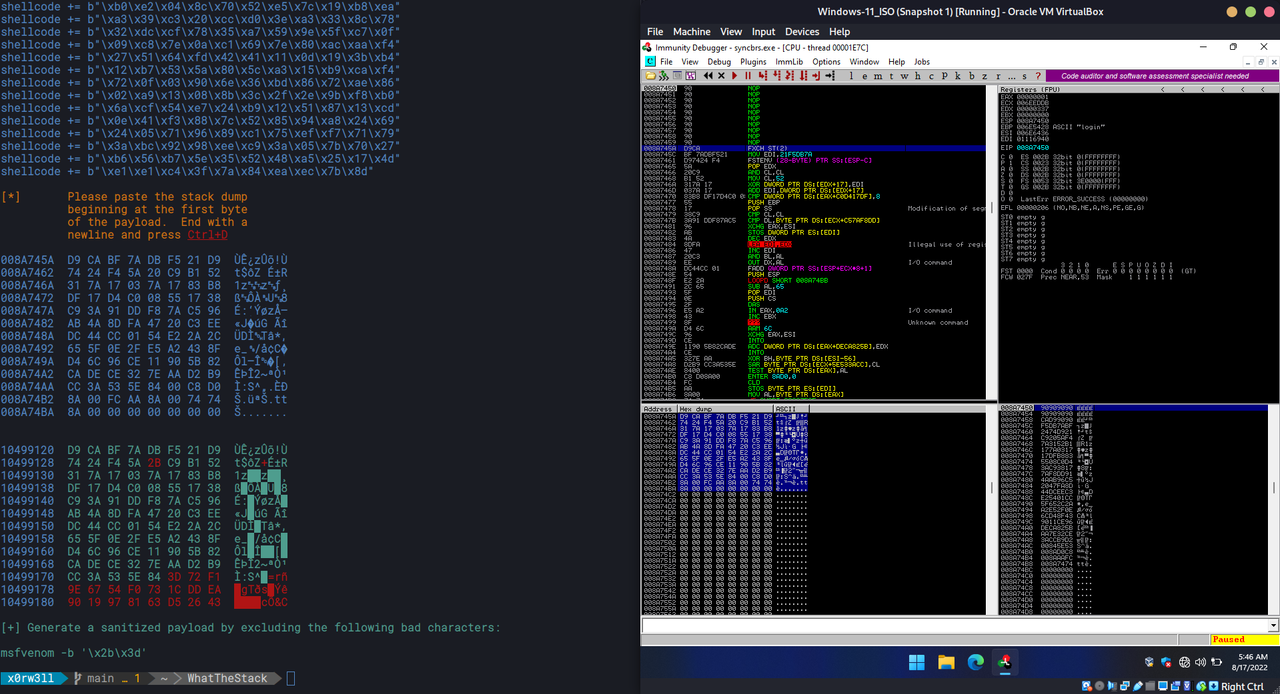
WhatTheStack can help you identify bad characters based on stack dump pasted from Immunity Debugger as-is.
It can also generate a python-friendly array of bad characters.
There are two core operational modes:
- badchars
- payload
badchars: compares stack dump against all characters [0x00:0xFF]
payload: compares stack dump against msfvenom shellcode
PEN-200 Students, but everyone else is more than welcome to use it as they see fit
# Tip: Consider adding the cloned repo to your $PATH environment to call the script from anywhere
# clone the repo into a location of your choice
$ git clone https://github.com/X0RW3LL/WhatTheStack.git
# cd into the repo after it's been cloned locally
$ cd WhatTheStack
# grant execute permissions to the script
$ chmod +x wtsThe following usage examples assume running the script from inside the local repo
$ ./wts -h
usage: wts [-h] [-v] [-u] [-i badchars|payload] [-g] [-b <badchars>] [-x]
options:
-h, --help show this help message and exit
-v, --version print version number and exit
-u, --update update to the latest version
core functionality:
-i badchars|payload identify bad characters - use against (badchars) [0x00:0xff]
or generated (payload) shellcode
-b <badchars> generate a badchar-excluded array (case insensitive): ./wts -b
'\x0a\x3d'
visual:
-g generate a variable containing all characters [0x00:0xff]
-x show example stack dump
- I noticed an
--updateoption. How does this work?- The script queries the GitHub repo for the current_version using the requests library. If versions mismatch, you're prompted to proceed. If you choose to do so, the script will pull the latest changes into your local repo
- Should I be worried about potential backdoors?
- The short answer: no
- The long answer: your concerns are valid, and I encourage everyone to practice due diligence by going through the code and keeping an eye out for changes. However, I would not 1) do something unethical, and 2) jeopardize my reputation by pulling off such a silly stunt
- How do I report bugs?
- You may create an issue with all the relevant bits of information; full Traceback calls, pasted payload and stack dump, and screenshots
- What about contribution?
- Contribution is highly encouraged. Create a PR and we may discuss it
- How can I contact you?
- You may reach out via Discord:
X0RW3LL#6548
- You may reach out via Discord:
Special thanks to the entire Offensive-Security team, as well as the amazing community that's helped me through my journey ❤️
Offensive-Security Official Website
Offensive-Security Community Discord