|
| About > About CME | |
|
Page Contents About CMEWhat Is CME?The Common Malware Enumeration (CME) initiative aims to provide single, common identifiers to new virus threats (i.e., malware) and to the most prevalent virus threats in the wild for the benefit of the public. Managed and maintained by The MITRE Corporation, CME is not an attempt to replace the vendor names currently used for viruses and other forms of malware, but instead to facilitate the adoption of a shared, neutral indexing capability for malware. Through the adoption of this neutral, shared identification method, the CME initiative seeks to:
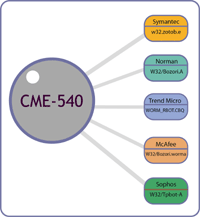
CME reduces confusion by assigning a single CME identifier to a particular threat so that anti-virus entities, as well as other security-related entities, can include it along with their proprietary information. In this way the public may cross-reference the disparate virus names through a common identifier. With CME, a 'threat' is a single entity encompassing any number of files that may be involved in a single incident. This is different from the previous course of anti-virus procedure in detecting and naming singular virus-related files. For example, with CME all components of Nimda—the IIS buffer overflow byte stream, the file that is passed through TFTP, the mass-mailed email it creates that attacks via the audio/x-wav vulnerability, the appended html pages or any of its other forms—are referenced by a single CME identifier. While the various anti-virus entities may still assign their own names, CME's common identifier enables network administrators to quickly identify the specific virus outbreak to which their organizations might be susceptible and to ensure that they are properly protected. CME is fashioned similarly to the Common Vulnerabilities and Exposures (CVE®) Initiative, which is also operated by MITRE and provides standardized names for computer vulnerabilities and exposures. As experience with CVE shows, once all parties have adopted a neutral, shared identification method, effective information sharing can happen faster and with more accuracy. CME identifiers will be assigned by the CME Submission Server from samples submitted by the CME Sample Redistribution Group, and made available to the public on the CME List on the CME Web site. Why CME?As outbreaks of computer viruses occur more and more frequently, anti-virus companies have had an increasingly difficult time staying coordinated with names for all of the new viruses. Because of this their products use a variety of names and variant designations for the same outbreak. This results in widespread confusion, with members of the public having to determine whether there is a single outbreak underway, multiple outbreaks, or a new outbreak altogether. Having to determine whether the protection they have in place is effective against current outbreak(s) also increases the public's burden further. As an example, spring 2004 was an extremely active period of virus outbreaks. Three or more Netsky variants appeared along with new variants of Mydoom, Bagle, and Beagle—all within days of each other. Network administrators had difficulty determining if their networks and systems were protected due to the variety of virus names that all referred to the same threat(s). An International, Community EffortWidespread adoption of CME's common identifiers will help the information security community and public communicate more effectively about malware outbreaks. Numerous anti-virus and other organizations are already participating. We encourage vendors to adopt CME identifiers in their products and services, and users to encourage your vendors to incorporate CME to support your enterprise security requirements. The CME initiative is industry-endorsed through the following: CME Editorial BoardEstablished in early 2005 to work with US-CERT and MITRE to help bring the CME concept to maturity and expand CME's reach to other members of the anti-malware community, the CME Editorial Board includes members from the international anti-virus community, including product vendors, testing organizations, and government. Many Board members also act as members of the CME Sample Redistribution Group, discovering and submitting possible threats for inclusion on the CME List. Oversight of the Board is provided by MITRE. Refer to the CME Editorial Board page for a complete list of the members to date. CME Sample Redistribution GroupThose industry organizations authorized to request a CME identifier from the CME Submission Server by providing a sample of the code they have identified as malware, along with as much supporting information as possible, for potential high-visibility outbreak threats. Refer to the CME Sample Redistribution Group page for a complete list of the members to date. Products and Services Including CME IdentifiersNumerous organizations are already including or have included CME identifiers in their anti-virus and information security products, services, Web sites, alerts, encyclopedias, etc. Refer to the Products and Services Including CME Identifiers page for a complete list of the organizations participating to date. How CME WorksThe public needs the most guidance during virus outbreaks. For that reason, the CME initiative will begin by addressing only the situations that satisfy outbreak conditions. Since most of the initial member organizations on the CME Editorial Board have representatives who also participate on the Anti-Virus Emergency Discussion (AVED) Network, CME will follow an approach similar to AVED's to identify high-visibility outbreak threats. Accordingly, one or more CME participants must determine that the threat is significant enough that all anti-virus vendors should offer an immediate defense for the threat to warrant a CME identifier. CME Identifier AssignmentWhen a qualifying threat occurs, a participating organization will request a CME identifier from the CME Submission Server. The participant will provide a sample and as much supporting information as possible. In response, CME's automated system will generate a CME identifier and redistribute the submitted information to the other authorized CME participants. The CME identifier and supporting information will then also be posted on the CME List on the CME Web site. Once the CME identifier has been attached to the sample and its corresponding threat, each CME participant will then disseminate the CME identifier as quickly as possible to those entities with which they regularly communicate in the industry and will reference the CME identifier in their products, on their Web sites, in communications with their customers, and when providing information to the press. (See the CME Process for a complete description of how a threat becomes a CME identifier.) CME Identifier ExplainedCME identifiers are assigned in the format 'CME-N' where N is an integer between 1 and 999, for example, "CME-123". To accommodate space-deprived anti-virus products, CME identifiers can be abbreviated (e.g., M123 or M-123), but the official format (i.e., CME-123) should be used in places such as Web pages, alerts, encyclopedias, etc. By minimizing the number of characters used initially, most anti-virus products will be able to add the CME identifiers directly to the names their products already display for users. Additional digits will be added when the remaining unused identifier space becomes too small. For the sake of successful text-based comparisons, leading zeros will always be omitted in an identifier, e.g., CME-00123 will always be written as CME-123. Each CME identifier recorded on the CME Web site includes following information associated with it:
As the list grows we will expand the information associated with each CME identifier in order to provide first responders with additional insights about the latest malware threats. DeconflictionIn order to reduce the assignment of duplicate identifiers to equivalent threats, CME has adopted the military process of "deconfliction." In CME, the first step in deconfliction occurs when a CME identifier is issued automatically. At this point, automated issuance of CME identifiers is turned off for the next two hours. This two-hour moratorium prevents messages that may have passed in ether to cause two CME identifiers to be issued for the same event. During the two hours following the issuance of a CME identifier, additional CME identifier requests will be deferred until the participants can decide whether the submitted samples constitute a new threat or are equivalent to the previous threat. If the participants agree that a submitted sample is a new threat, then an additional CME identifier can be "forced." See the CME Process page for a detailed description of deconfliction. Take the Next StepWidespread use of CME's common identifiers will help the information security community—and the public—communicate more effectively about computer virus outbreaks, thereby severely reducing the extensive confusion that occurred in the past. For example, before CME one anti-virus product might name a single computer virus 'NewOutbreak.A!M-555' and a second 'OldFamily.CC!M-555', but with the CME initiative a single, common CME identifier will show that it is the same threat. Adoption of CME among anti-virus product vendors is critical. We strongly encourage users of anti-virus products to ask their preferred vendors to adopt CME identifiers. For anti-virus product vendors, supporting and participating in the CME initiative is a bold first step in announcing to your users that you want to help alleviate their confusion and further protect their systems and networks. While technical challenges to having all anti-virus products use the same name for a threat at the start of an outbreak certainly exist, these challenges are greatly reduced once the initial outbreak occurs. Adopting the use of CME identifiers is a significant first step in establishing a consistent approach by anti-virus entities that will benefit users and the entire information security community. Contact us at cme@mitre.org to discuss how you and your organization can help this growing anti-virus and information security initiative. |
||
|
|
||