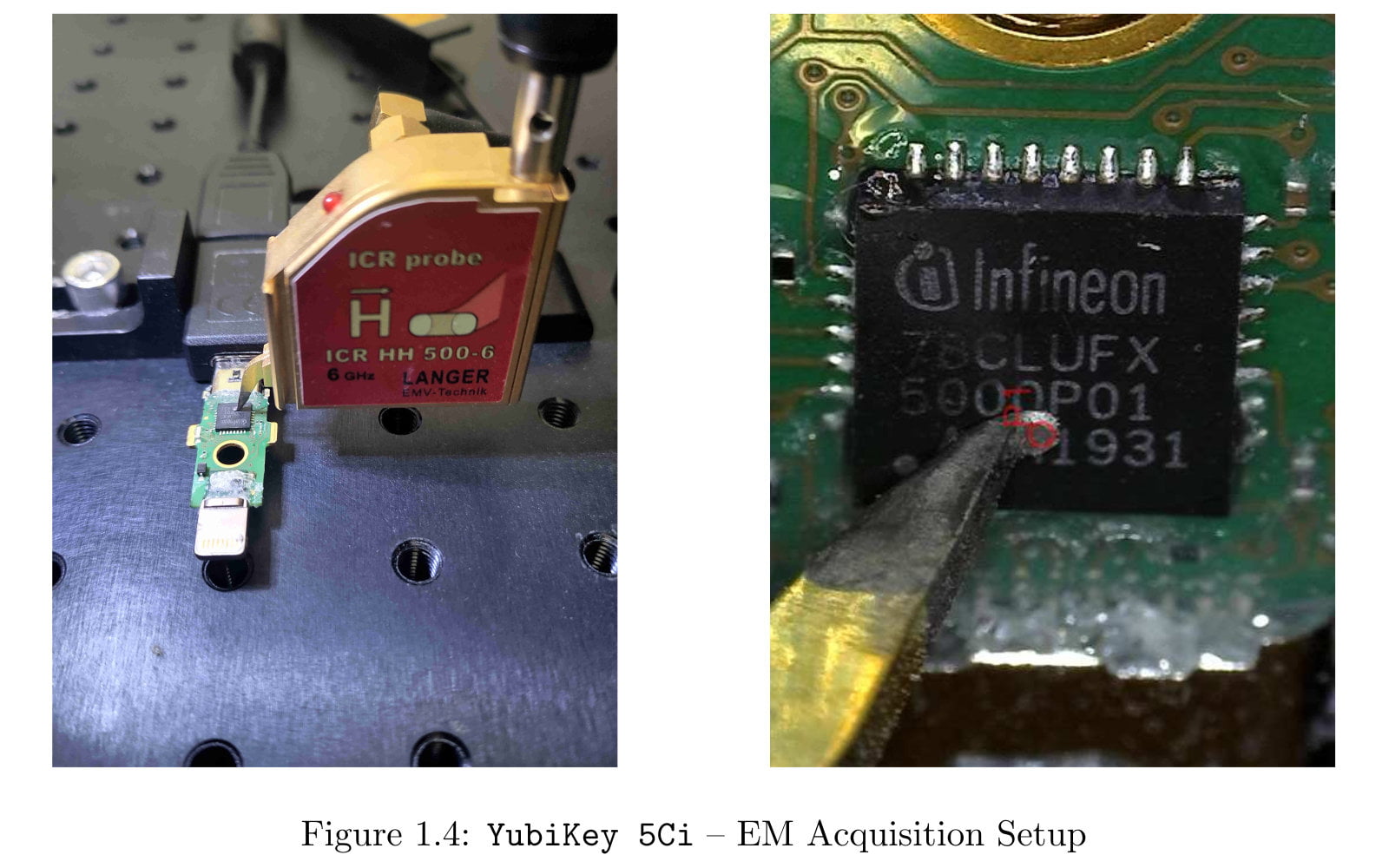
It looks like everyone's favourite FIDO token provider might have an unpatchable vulnerability! Much Sturm und Drang from the usual sources. But how bad is it really? Not so bad - but it does expose some weaknesses in the very idea of having physical tokens. First up, as the research paper's abstract says: The attack […]
Continue reading →

This book is outstanding. It's the mid 1980s, you're administrating a nascent fleet of UNIX boxen, and you are tasked with accounting for a 75¢ billing discrepancy. Naturally that eventually leads into an international conspiracy involving the FBI, NSA, and an excellent recipe for chocolate chip cookies. It is a fast paced, high-tension, page turner. […]
Continue reading →

A bit of a thought experiment - similar to my Minimum Viable XSS and SVG injection investigations. I recently found a popular website which echoed back user input. It correctly sanitised < to < to prevent any HTML injection. Except… It let through <h2> elements unaltered! Why? I suspect because the output was: <h2>Your search […]
Continue reading →

This is a diary of what I've learned. Hopefully it will let other learners know what the course is like, and if it is worthwhile. Oh, and it might just help me remember what I'm learning! Verdicts Some of the lab tasks were impossible without looking at the cheat sheet. I got stuck on one […]
Continue reading →

This is a diary of what I've learned. Hopefully it will let other learners know what the course is like, and if it is worthwhile. Oh, and it might just help me remember what I'm learning! The penultimate day. Try not to worry about the upcoming exam! Today was lots of HTTP, TLS, and other […]
Continue reading →

This is a diary of what I've learned. Hopefully it will let other learners know what the course is like, and if it is worthwhile. Oh, and it might just help me remember what I'm learning! Day 3 - the day I was dreading most of all… Windows! I've been avoiding M$ WinDoze (LOL!!!) since […]
Continue reading →

This is a diary of what I've learned. Hopefully it will let other learners know what the course is like, and if it is worthwhile. Oh, and it might just help me remember what I'm learning! Day 1 was all about password cracking and metasploit. Today? Linux Hacking! Sadly, we aren't learning anything to do […]
Continue reading →

As part of my MSc, I have to take three "Professional Practice" courses. The course provider, QA.com, let me choose anything from their online catalogue. The first I'm doing is Certified in The Art of Hacking. As regular readers will know, I'm pretty reasonable at hacking. I have received bug bounties from Google, Twitter, Samsung, […]
Continue reading →

This is a two-part blog post about rewriting the rules. I hated playing sports as a teenager quelle surprise. In a vain attempt to get me to love the beautiful game, a PE teacher once made me team captain for a kickabout. My rival? Sporty Dave. Head boy, house captain, and conqueror of puberty. The […]
Continue reading →
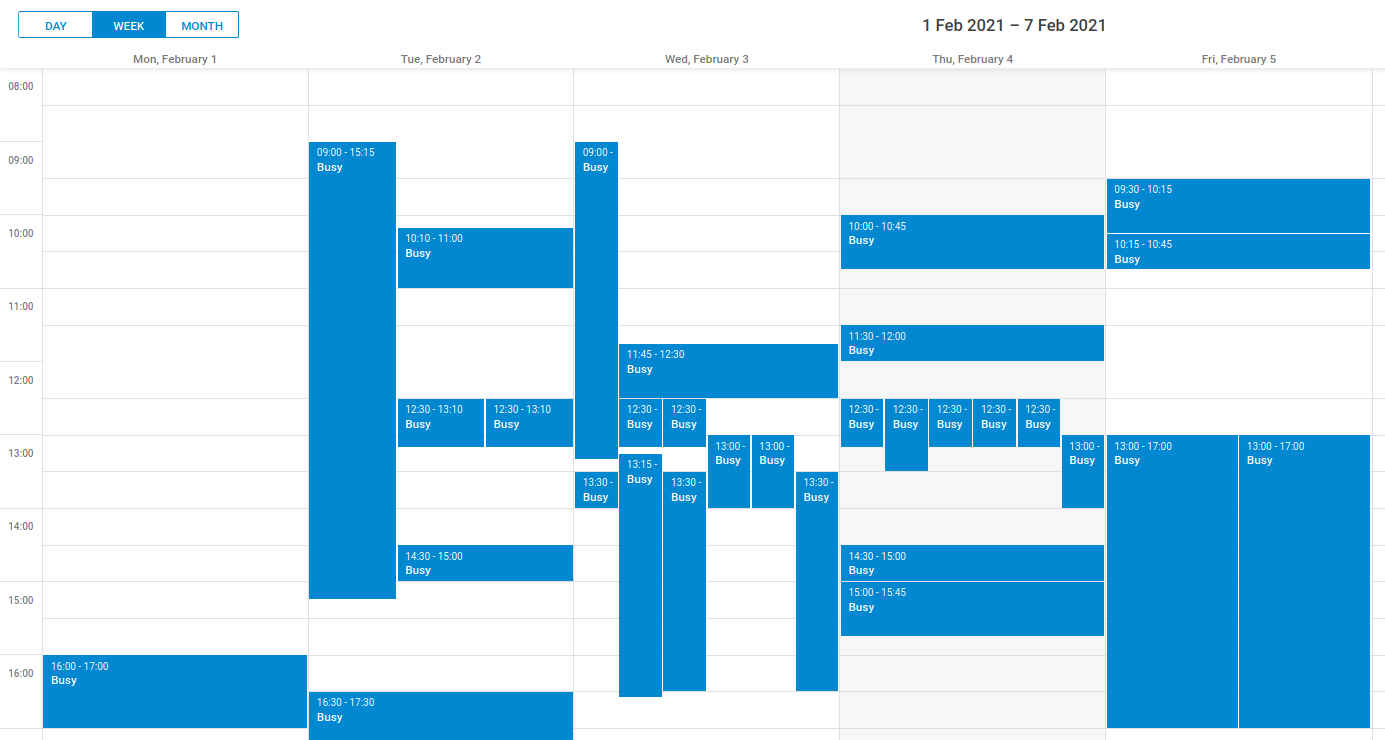
Last year, I blogged about why I make my work calendar public. It is useful to have a public website where people can see if I'm free or busy. But the version I created relied on Google Calendar which, sadly, isn't that great. It doesn't look wonderful, especially on small screens, and is limited to […]
Continue reading →





